IAM

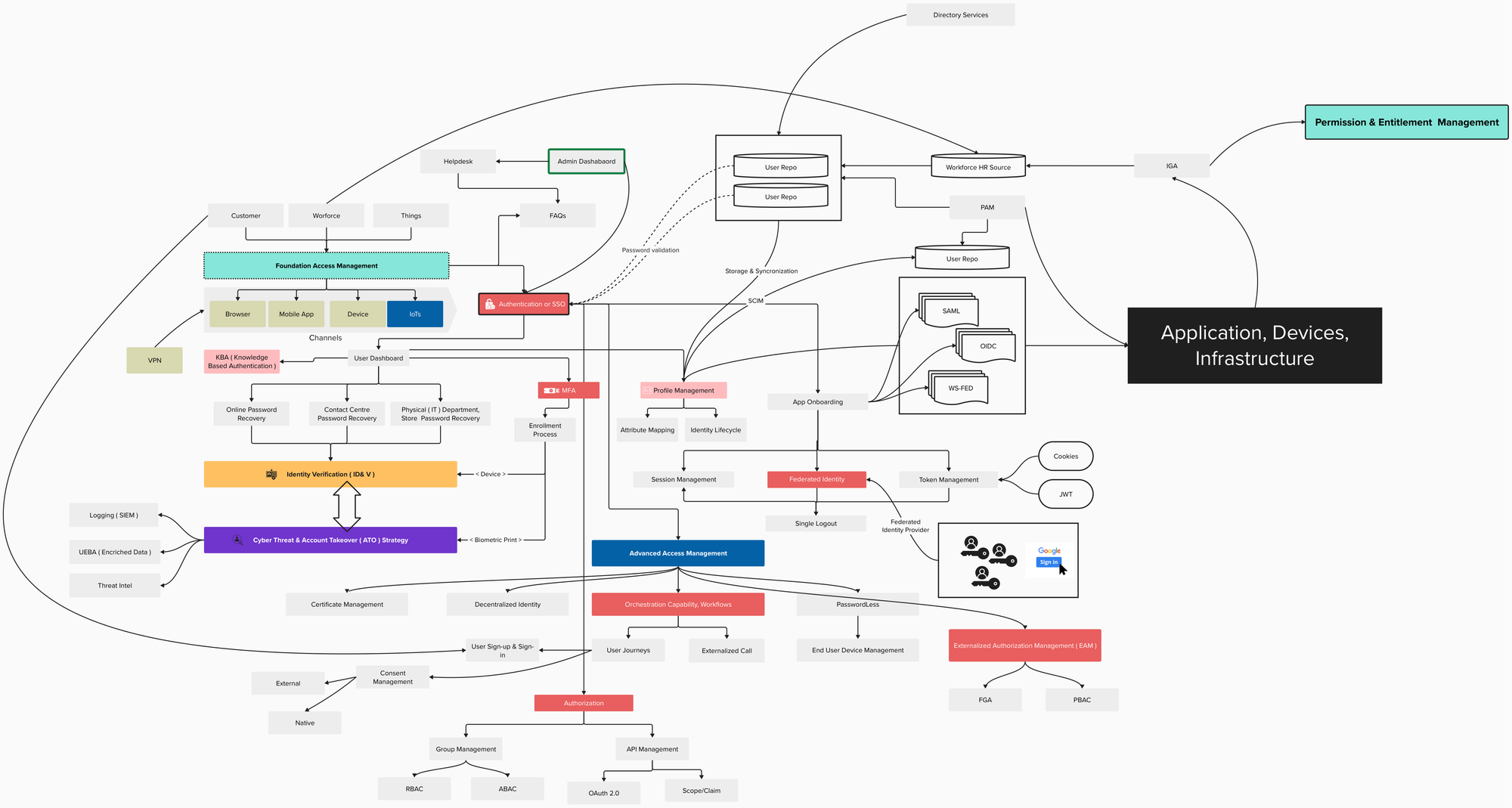
Building an Extensive IAM Architecure
Understanding IAM Architecture Features as an IAM Architect
An IAM architect requires
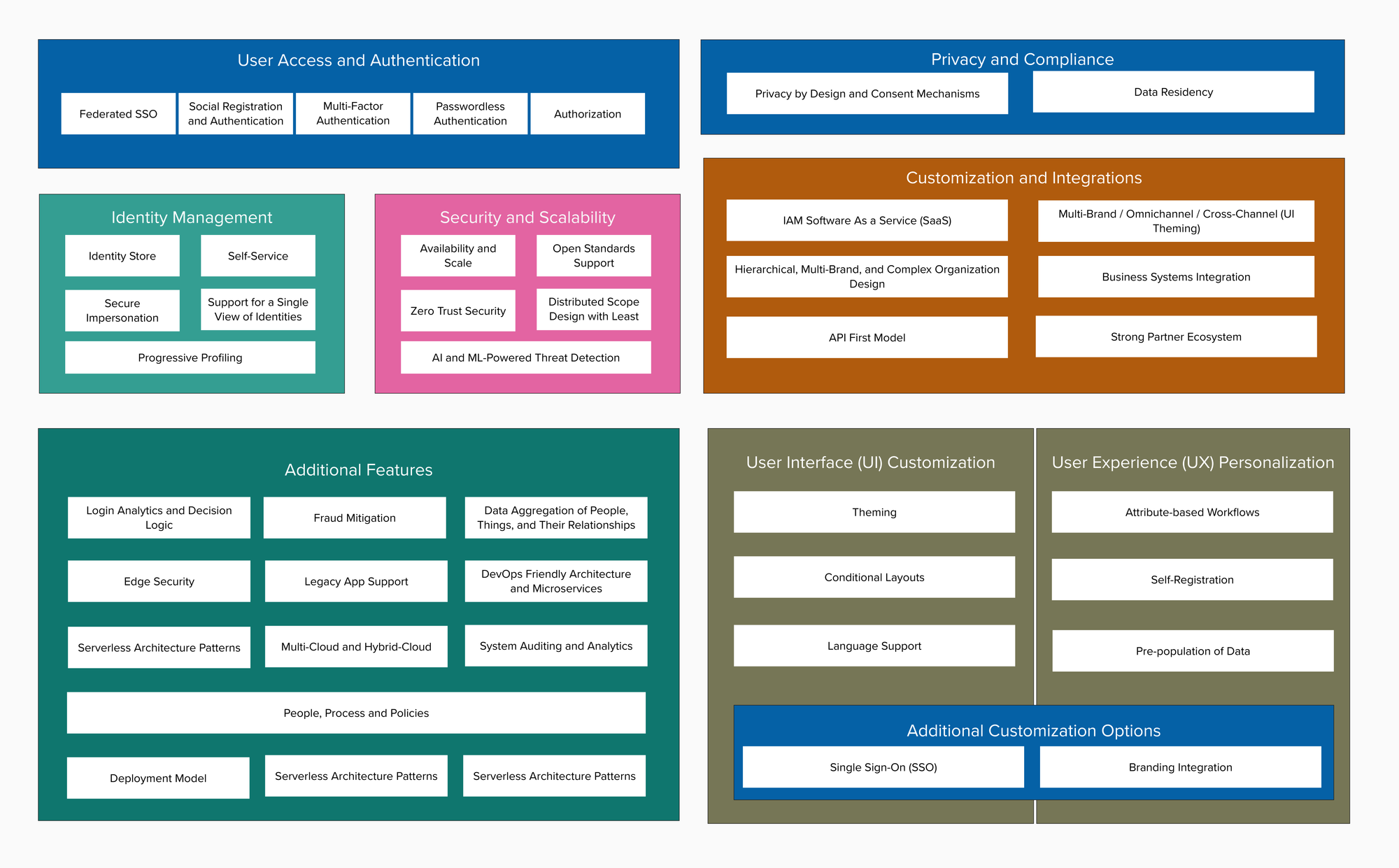
IAM Architect 101 Series
Understanding the Architectural Journey
Becoming an IAM Architect involves more than just
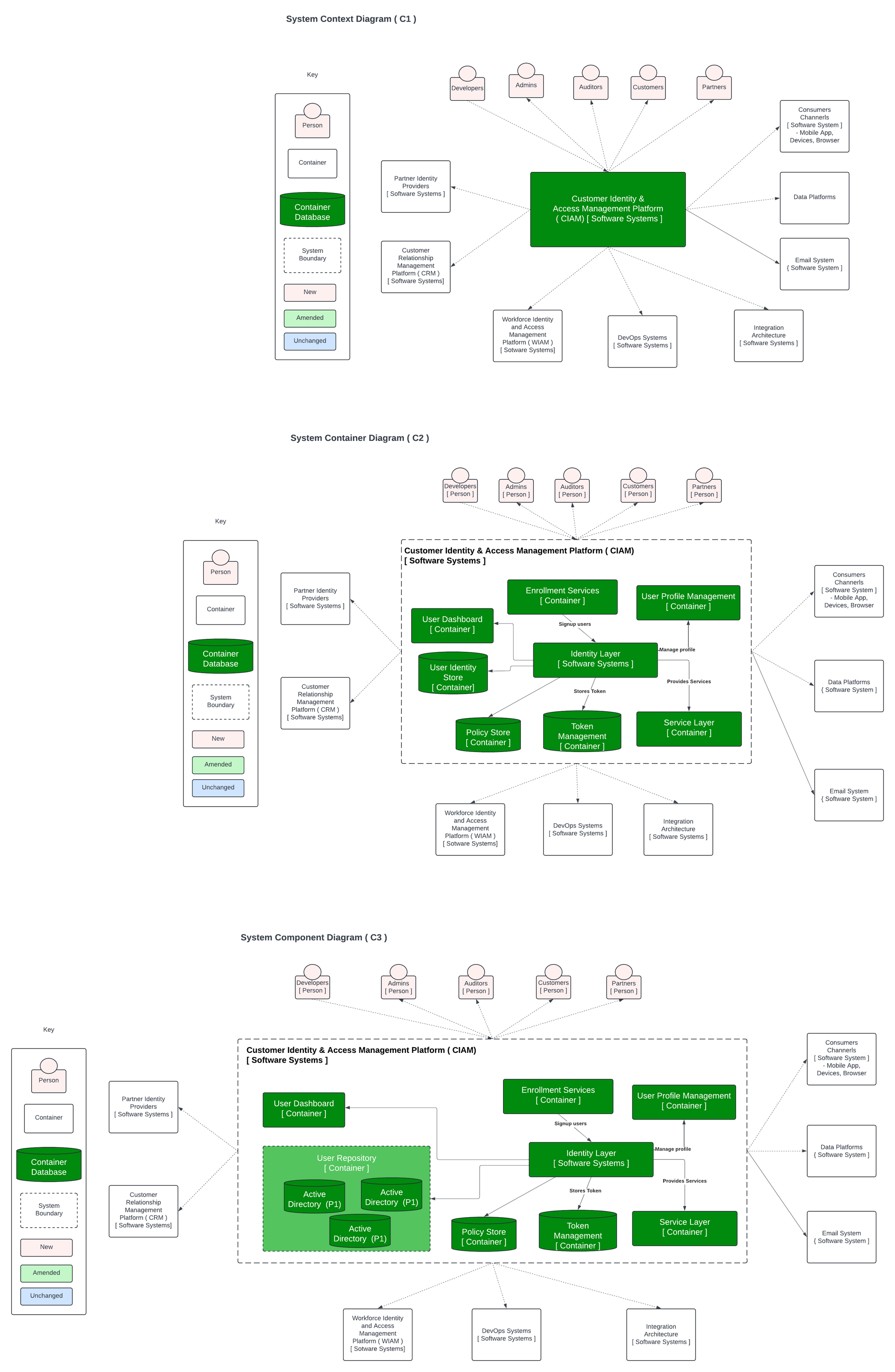
Understanding AM vs IGA Features
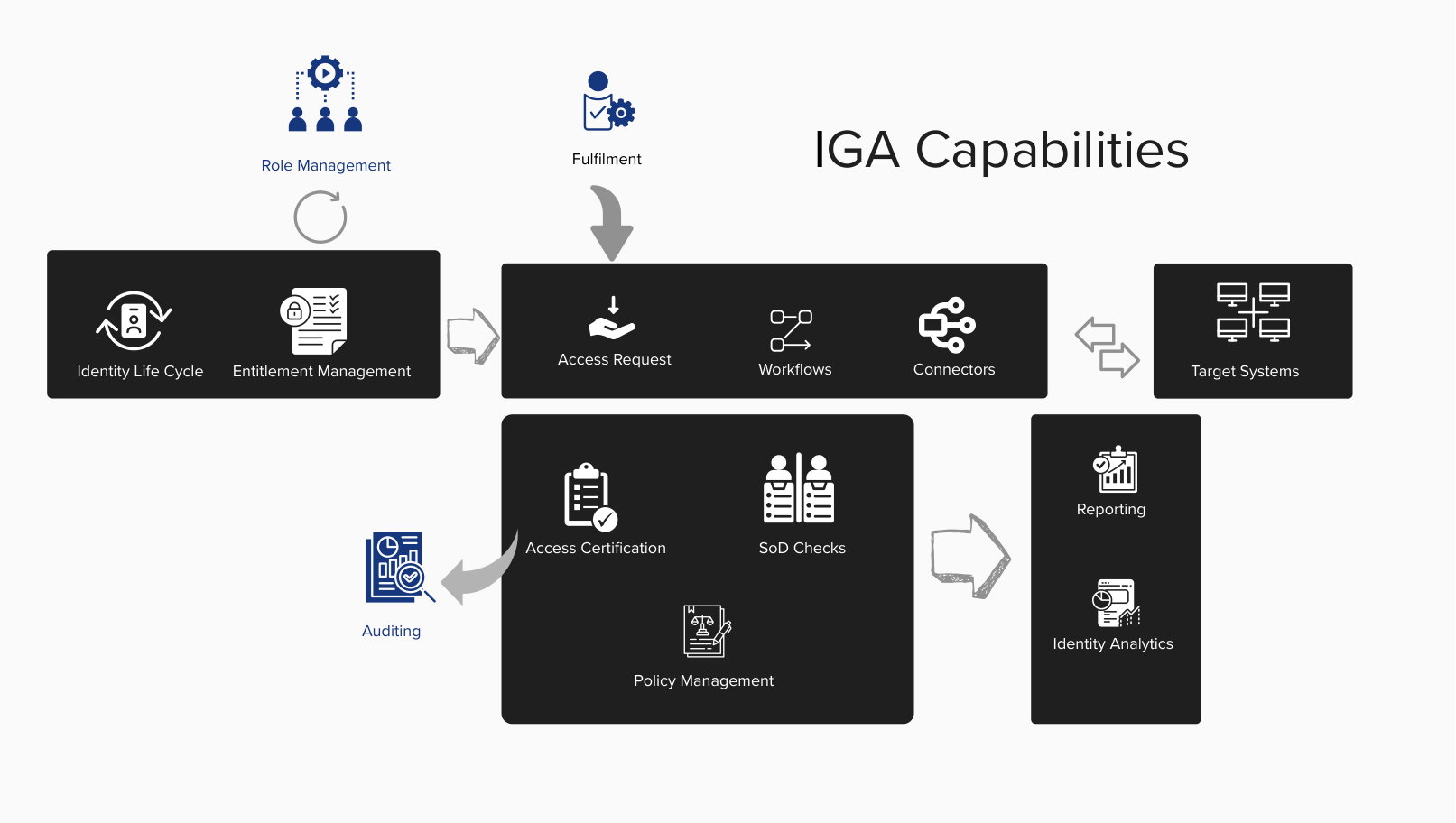
IGA Capabilities
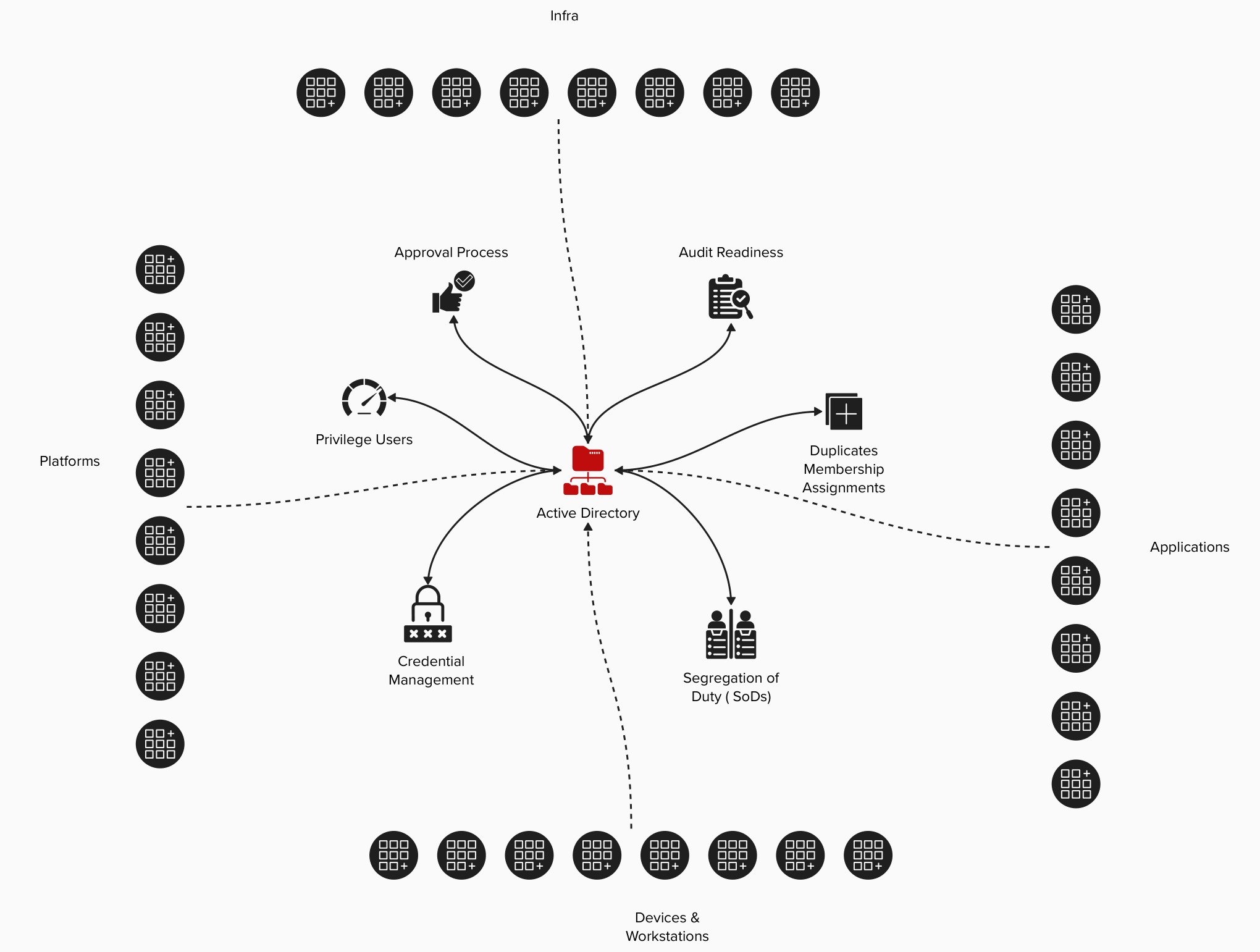
AD > Azure AD > Entra ID > ..and then to the write-back
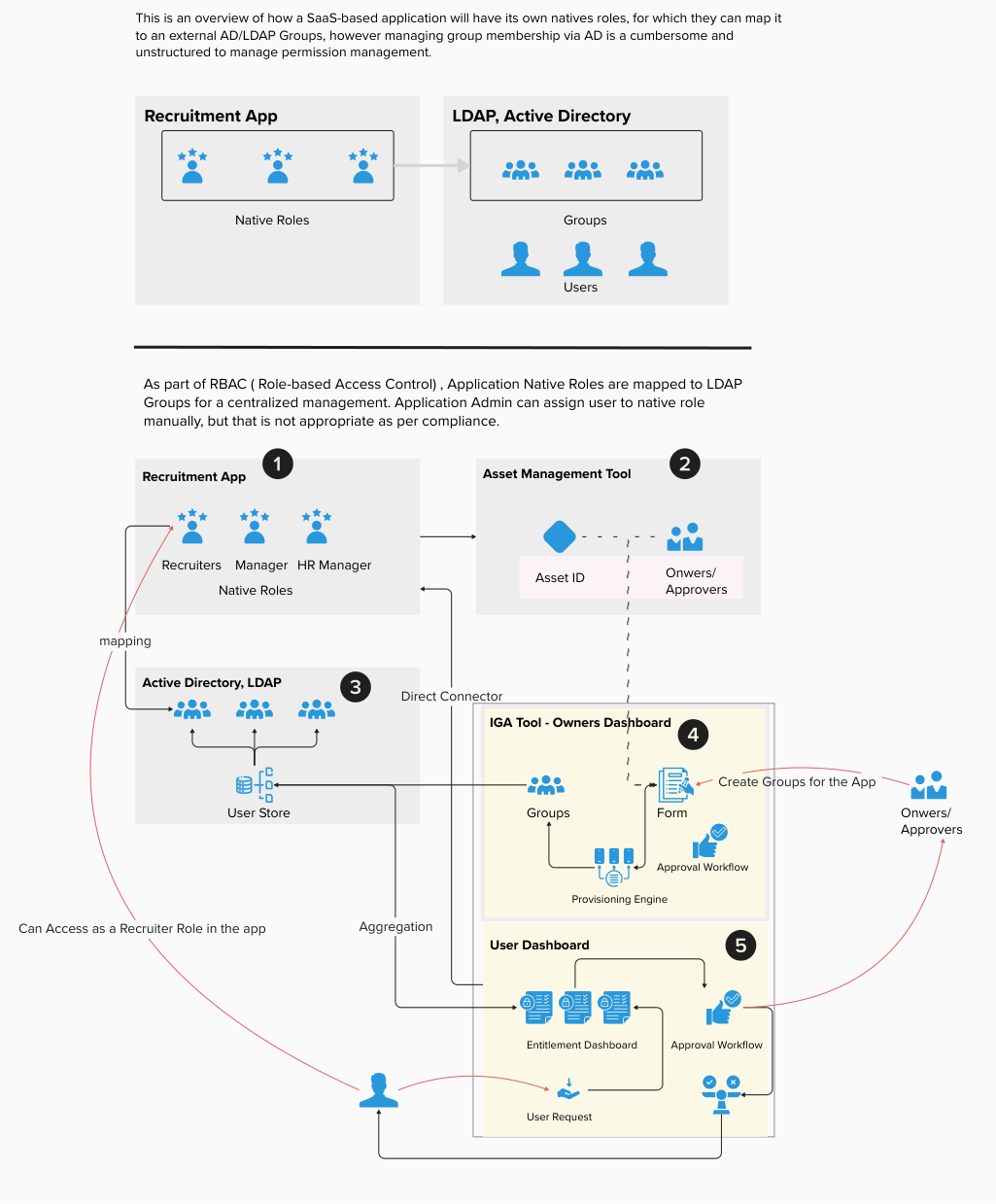
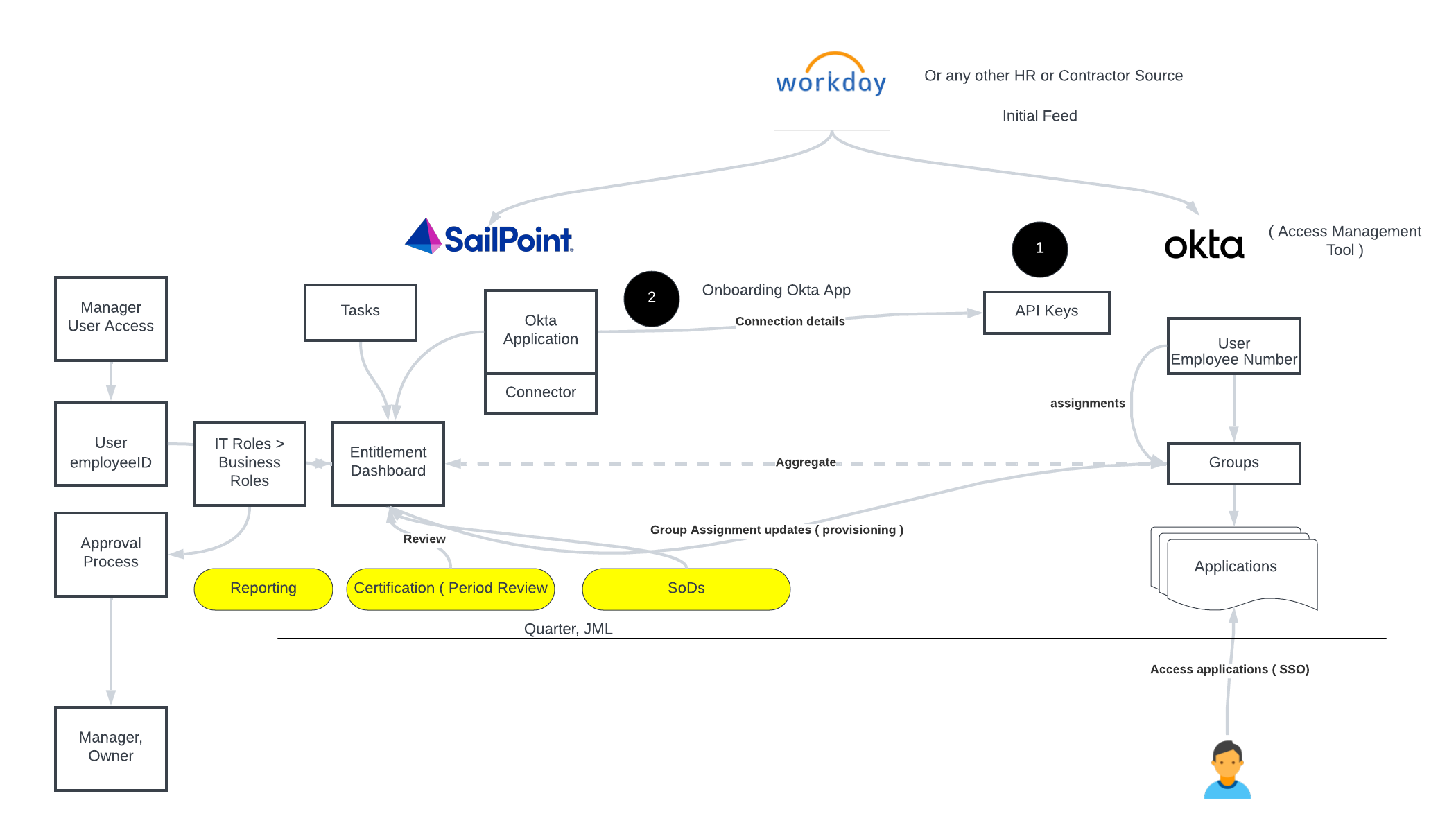
Automate Permission Management via IGA Tools ( SailPoint, Saviynt )
Let's dive into entitlement management in a business context and
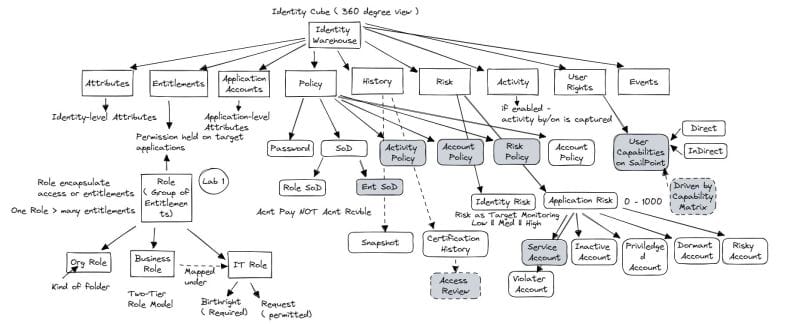
Learning SailPoint IIQ
SailPoint is a leading IAM solution that helps organizations manage user identities,
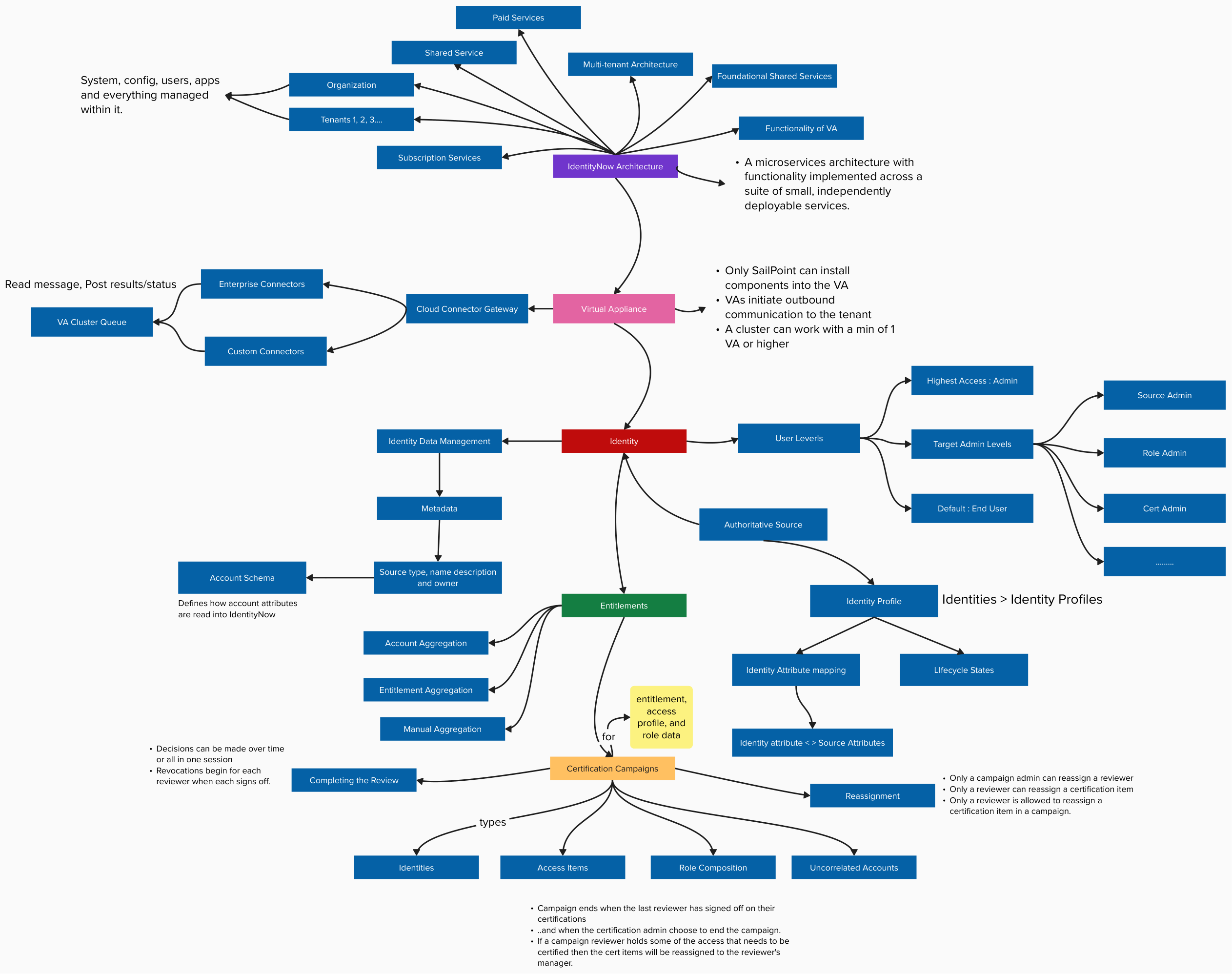
SailPoint IdentityNow Learning Series - 1
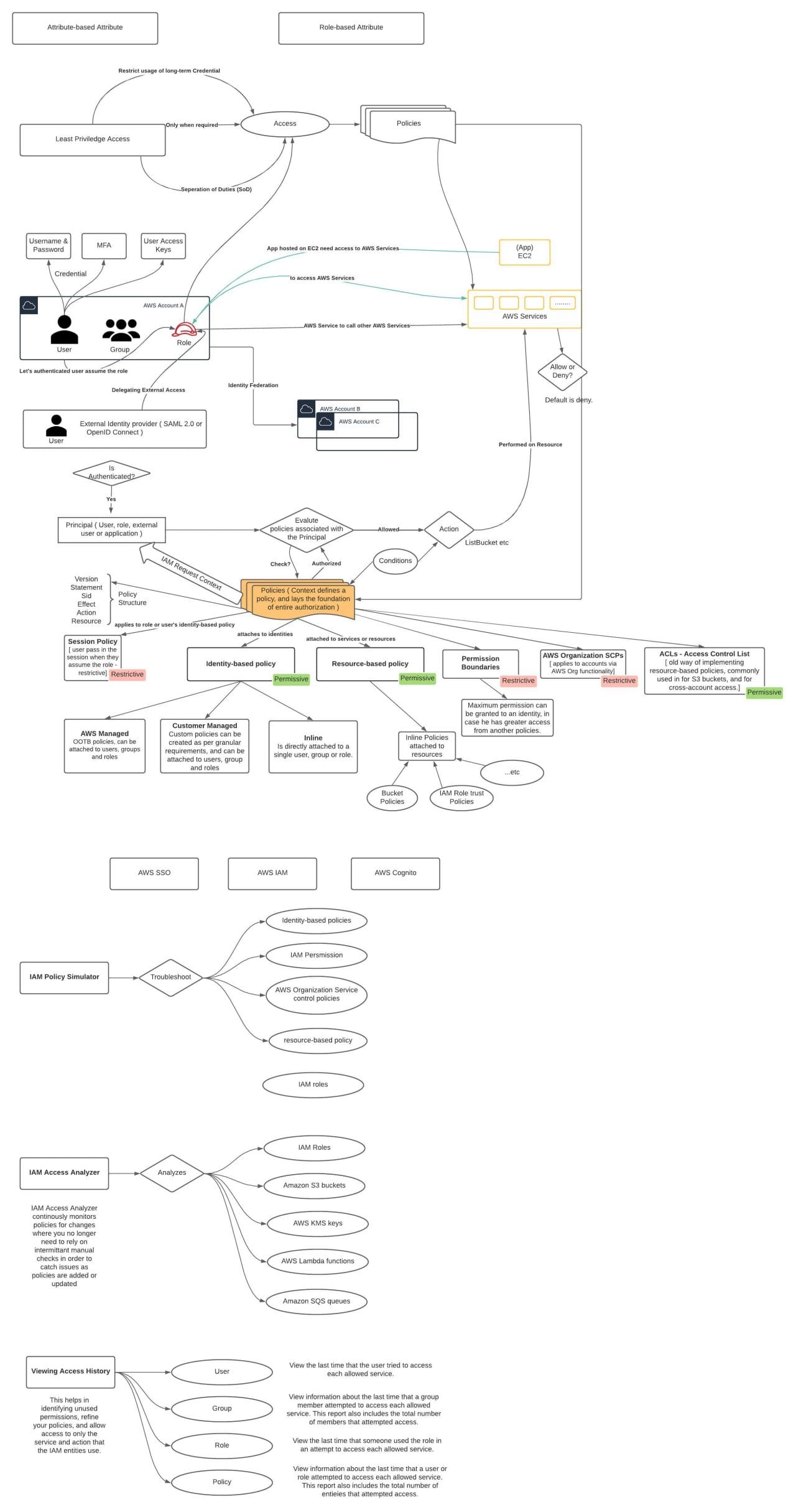
AWS IAM 101
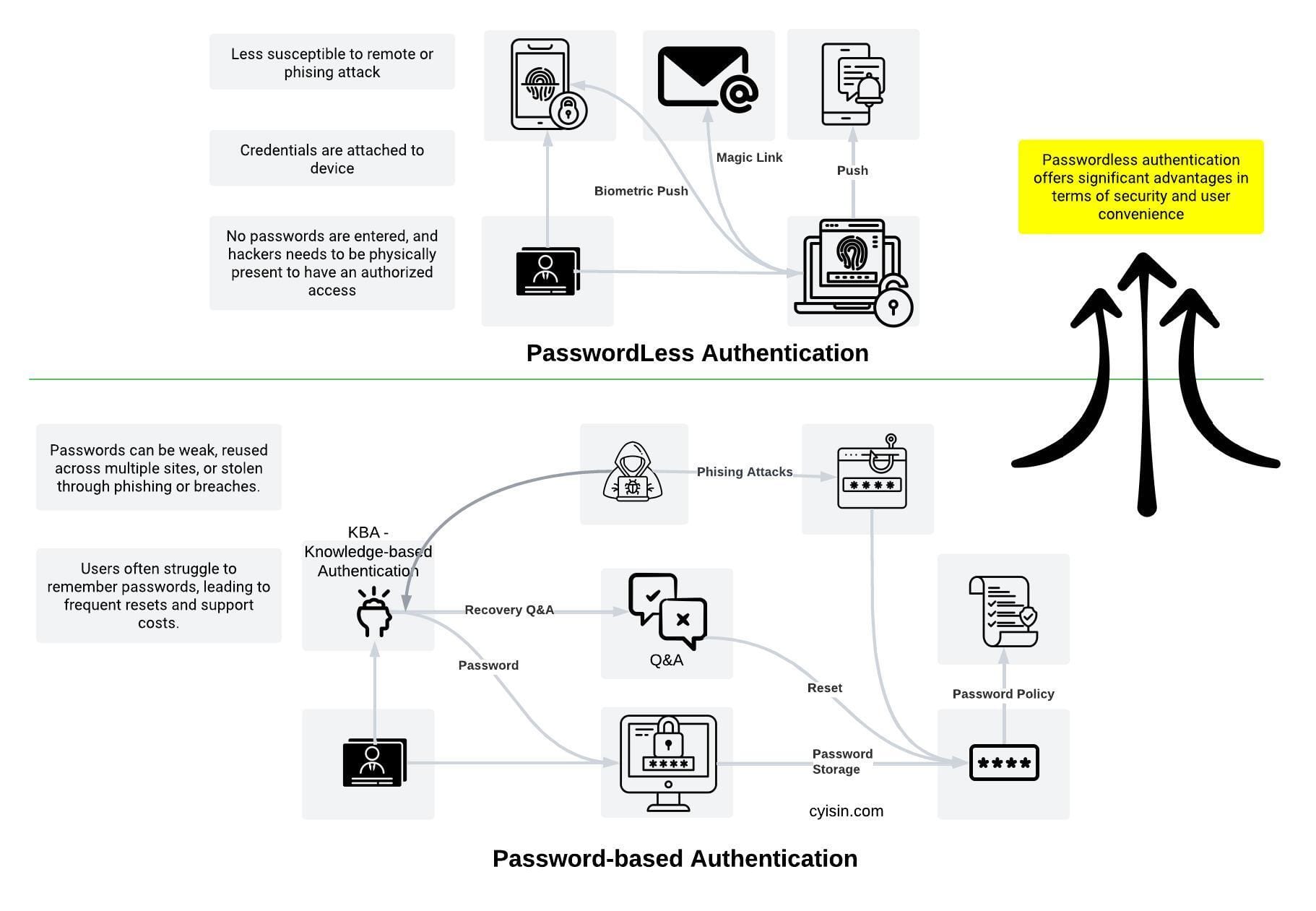
What is PasswordLess Authentication?
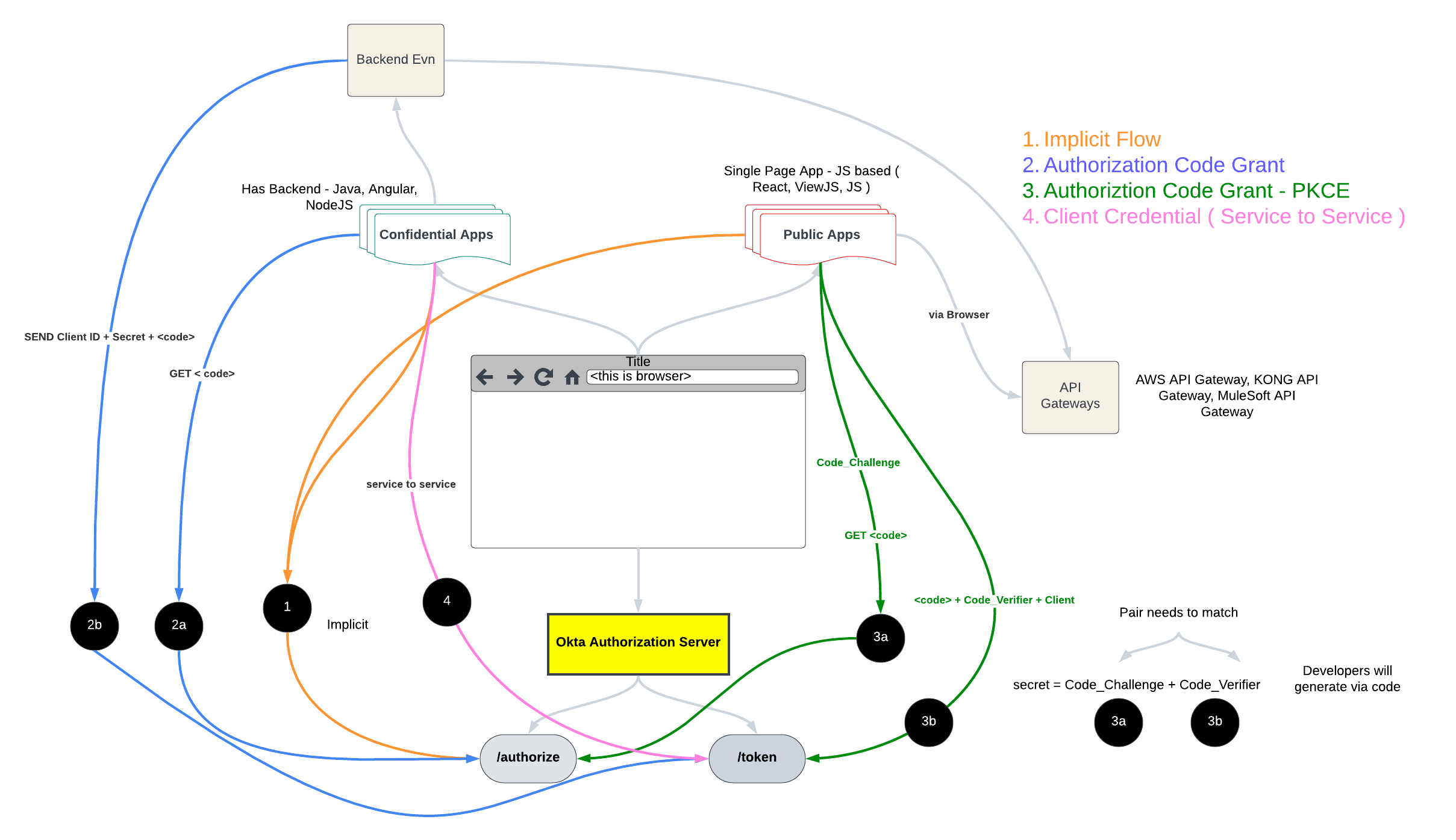
Types of Application - Confidential vs Public Clients
I have asked this question multiple times during Interviews :
What are the