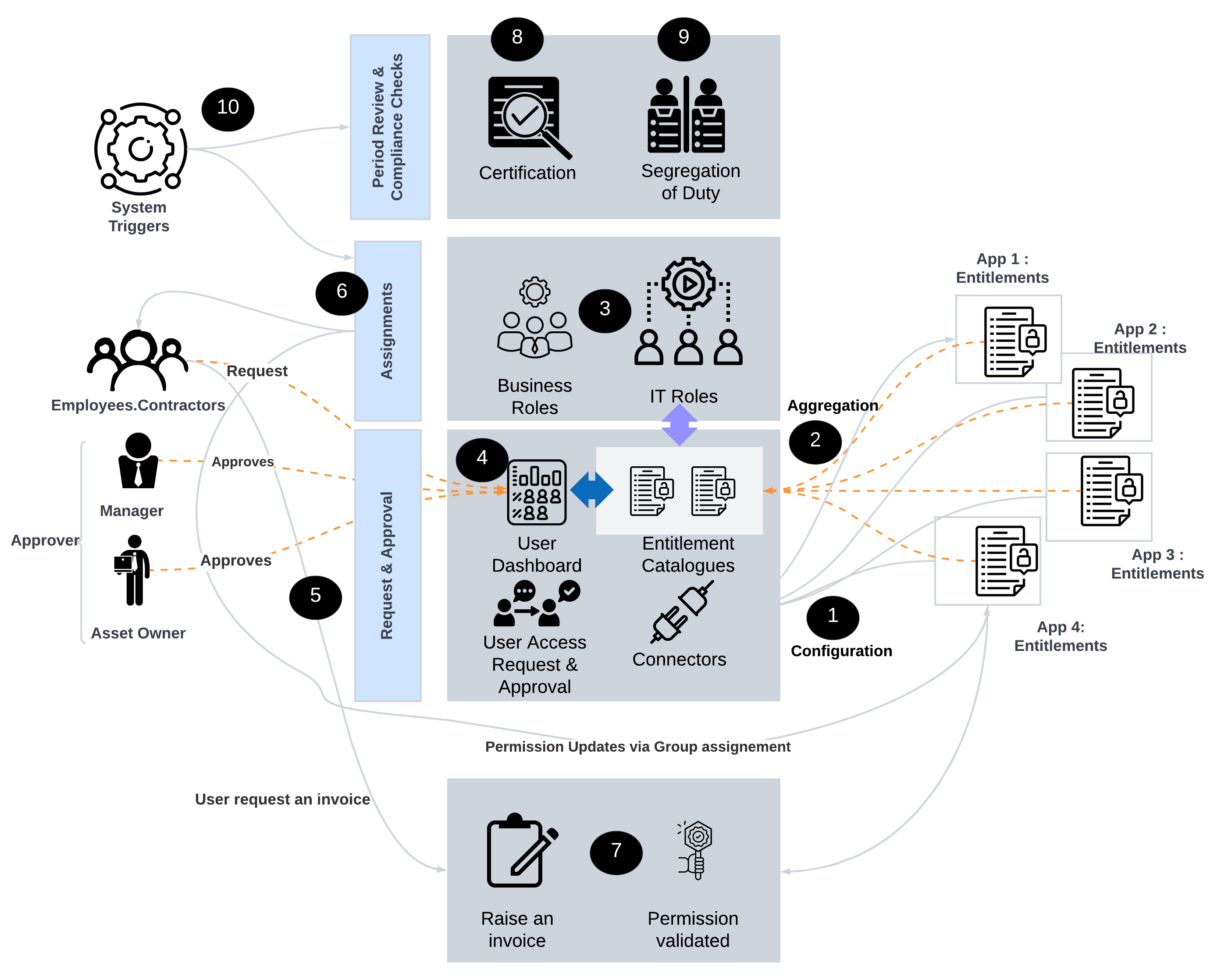

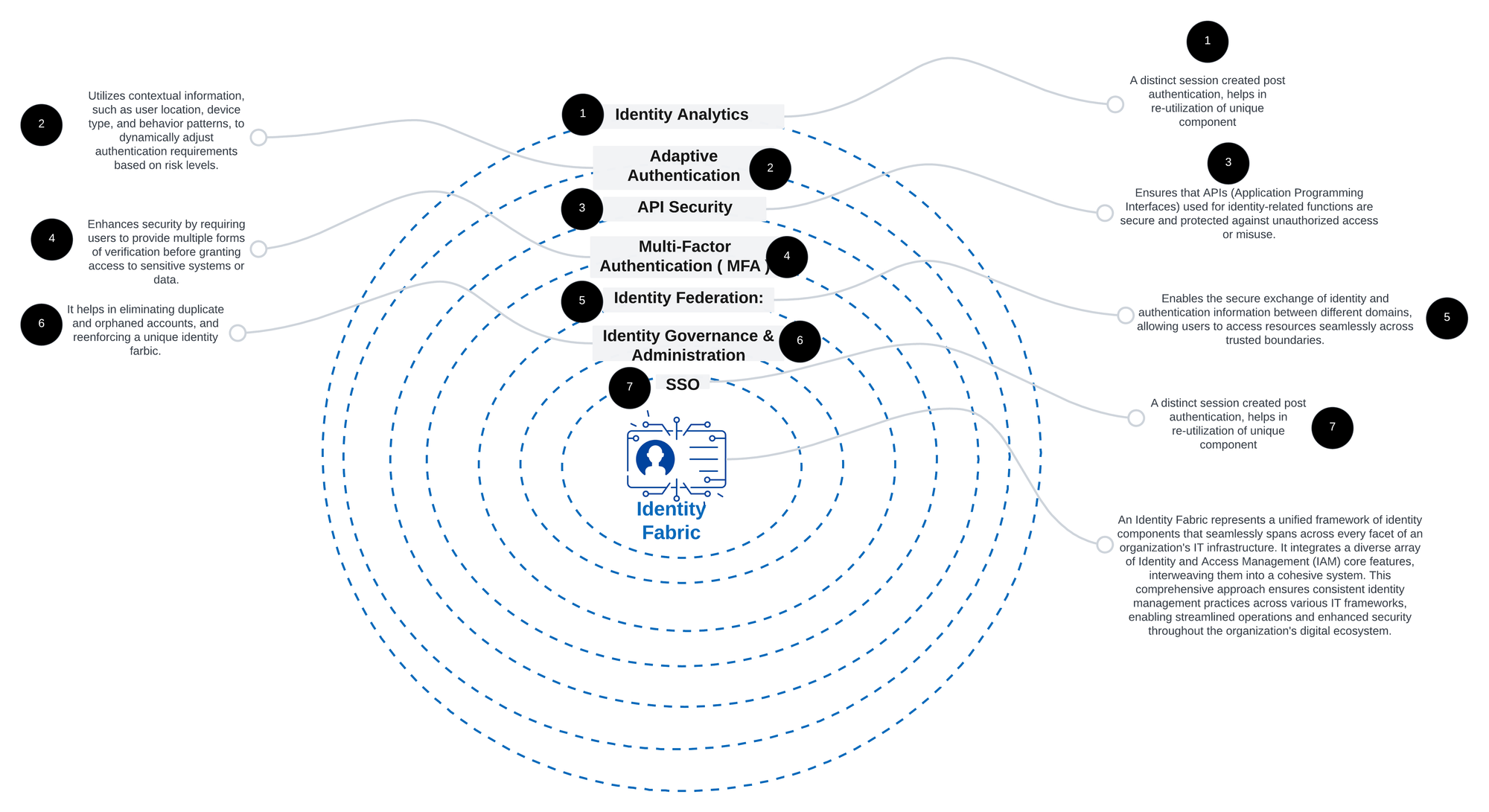
Identity Fabric
🔒 Unlock the Power of Identity Fabric 🔒
Identity Fabric is the ultimate nirvana
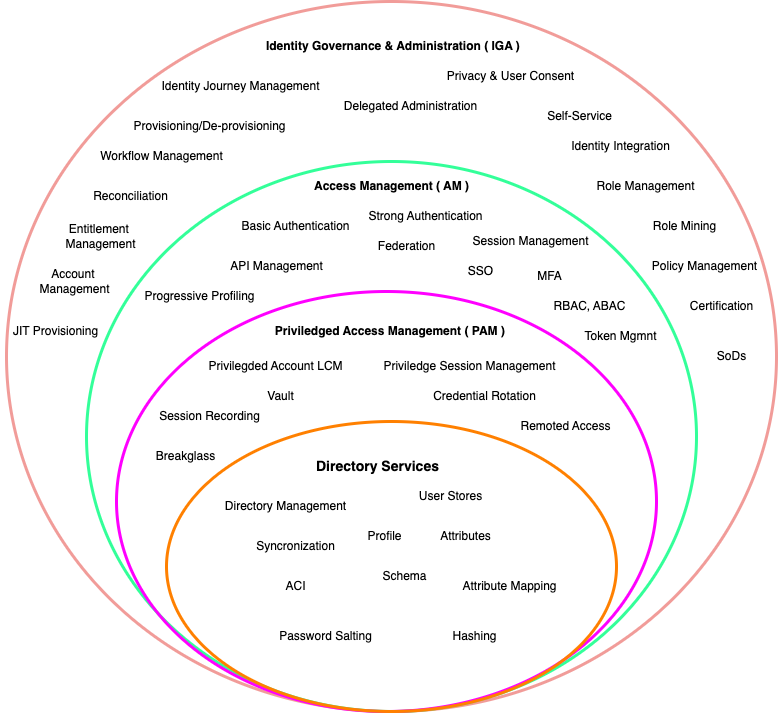
IAM Pillars
🔒 Embracing the Pillars of IAM: Directory Services, PAM, AM, and IGA
🔒In
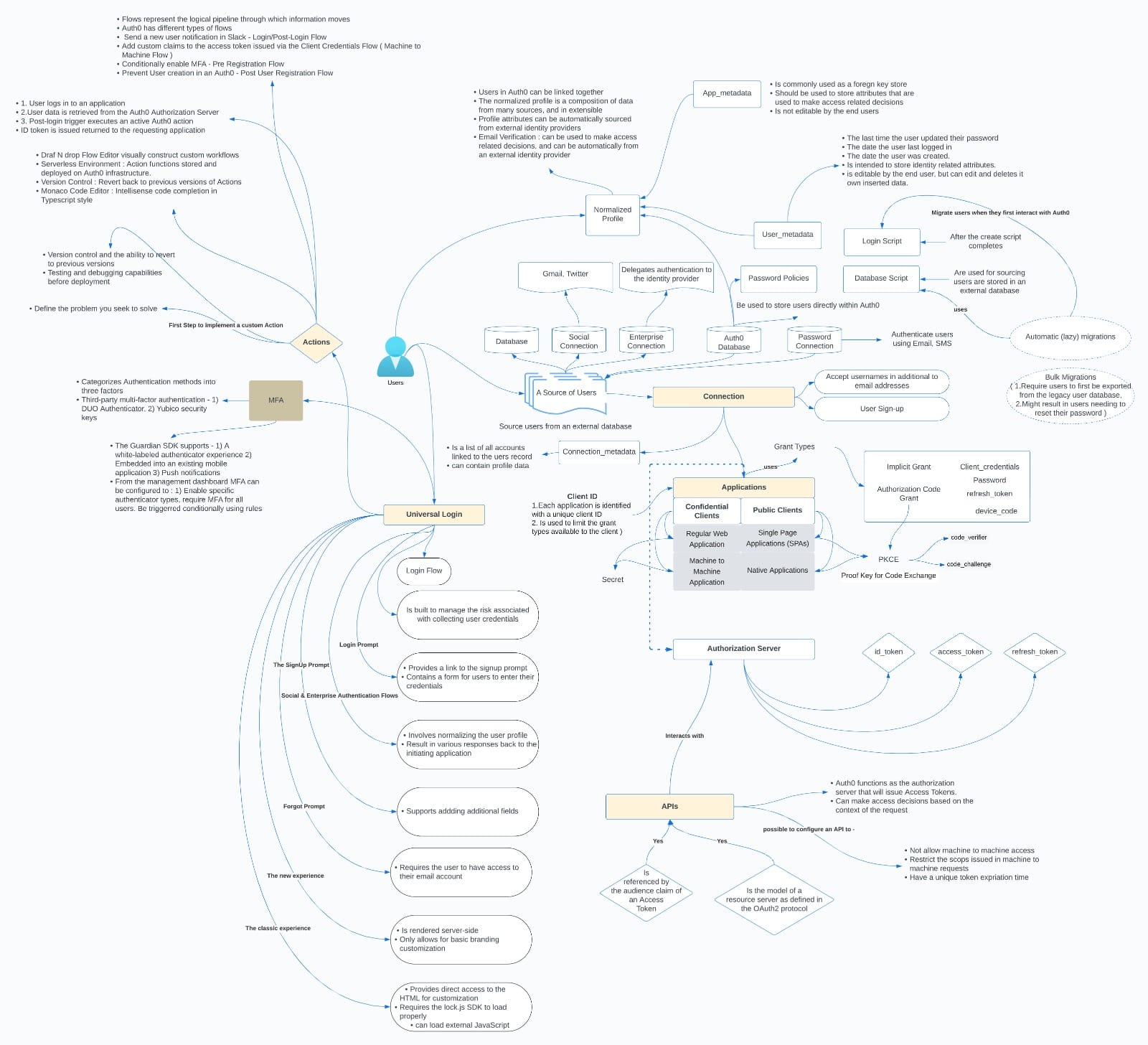
Auth0 - A CIAM Tool
When it comes to CIAM, there are primarily three major enterprise tools
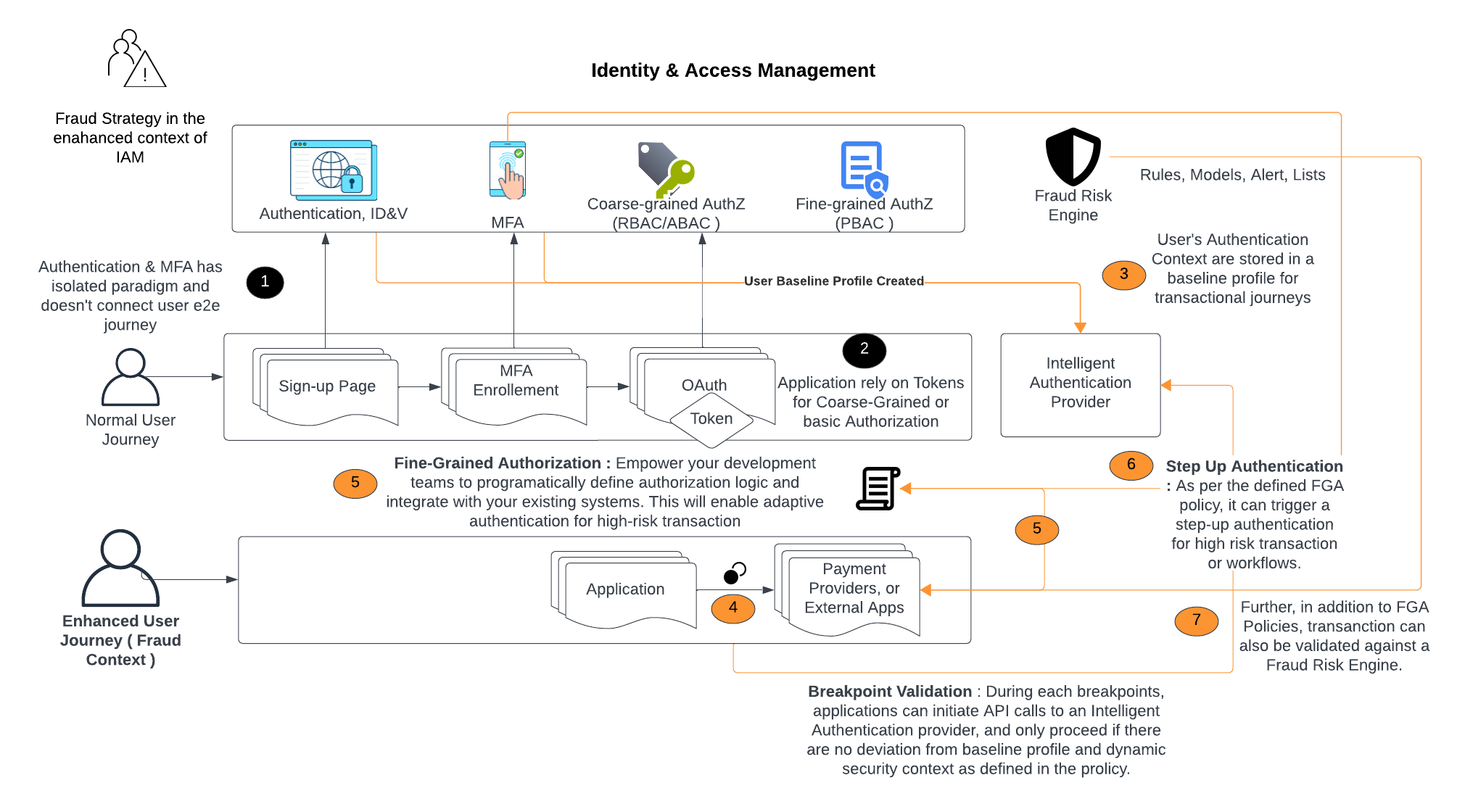
Identity and the Fraud Context
The image above depicts a flowchart illustrating an enhanced identity and access
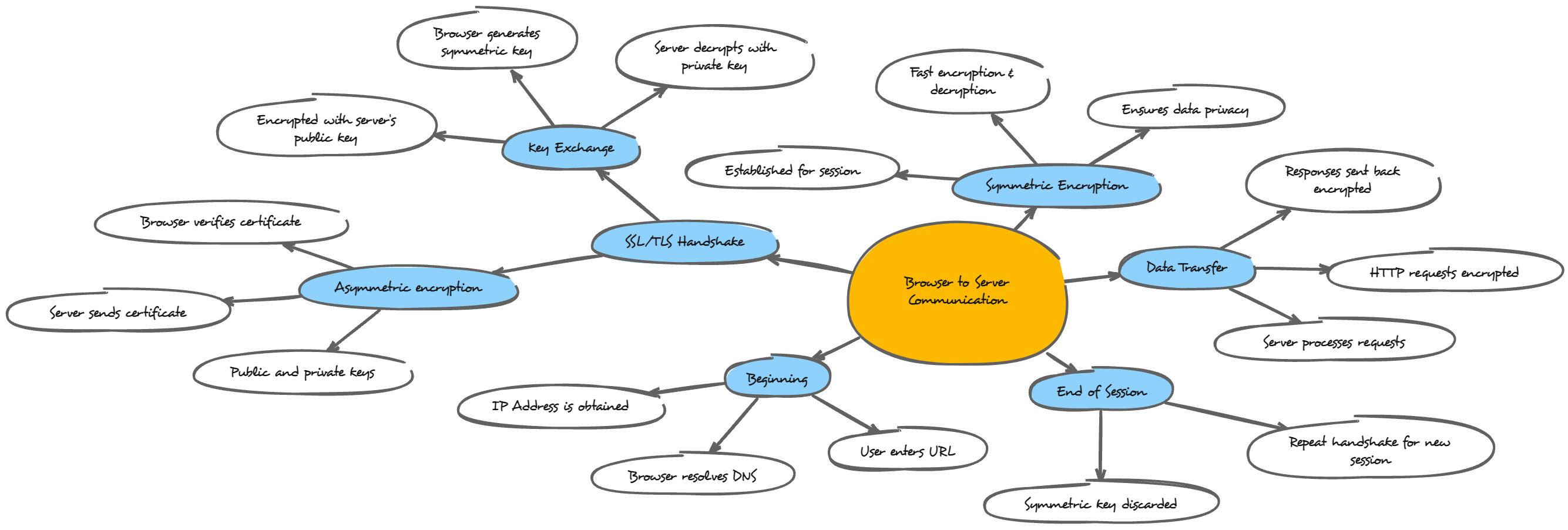
SSL and Browser Security
Browser initiates HTTPS session
* This refers to a web browser starting a
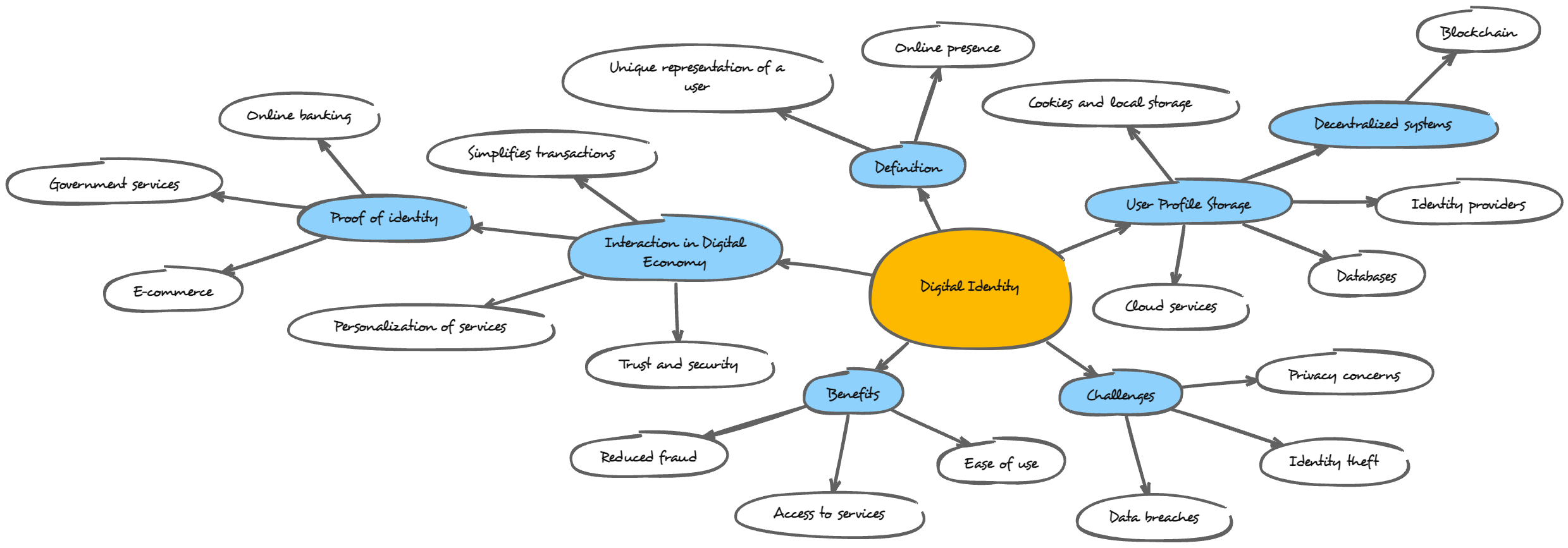
Digital Identity
Online Presence
* Online Banking: Conducting banking transactions electronically through a bank'
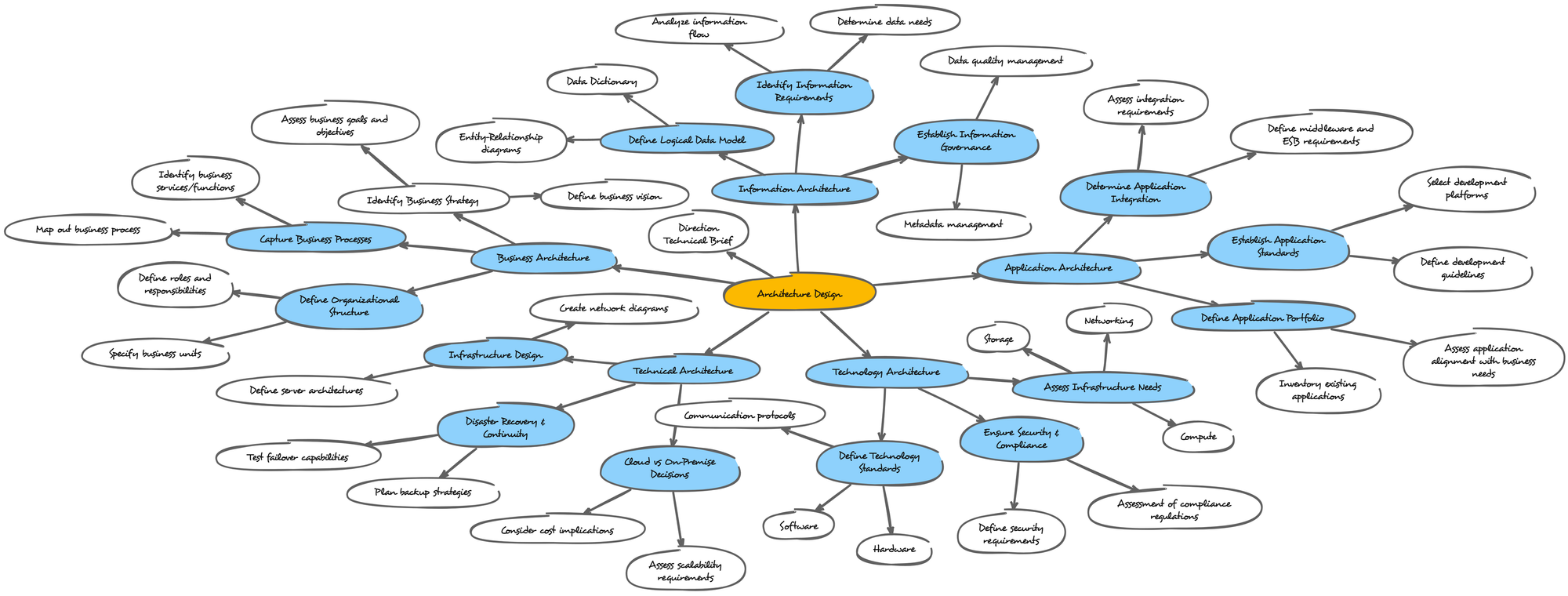
Architecture Design
Have you even been asked to explain about various architecture, how does
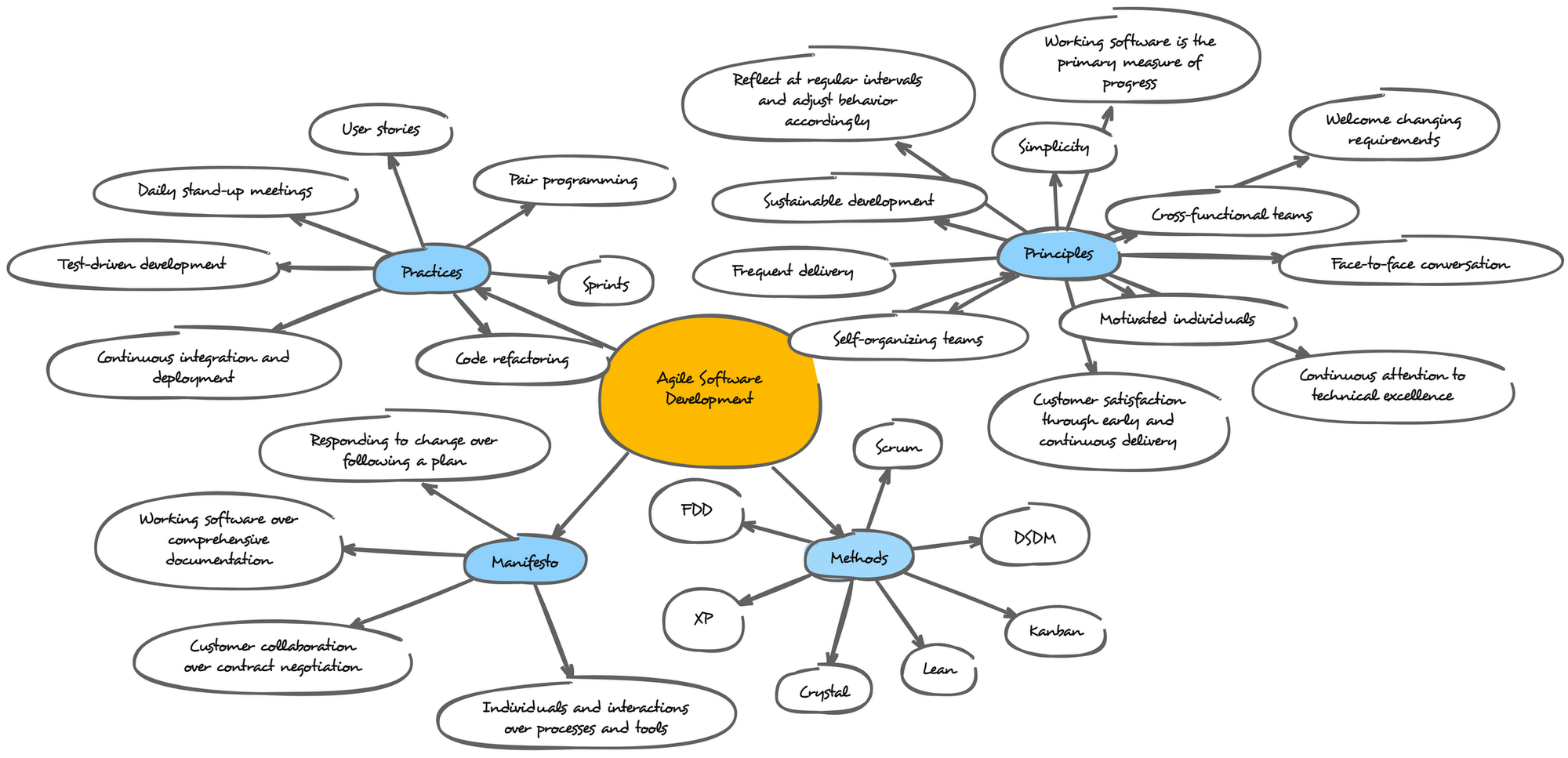
Agile Software Development
The image attached depicts a flowchart illustrating the Agile software development methodology.