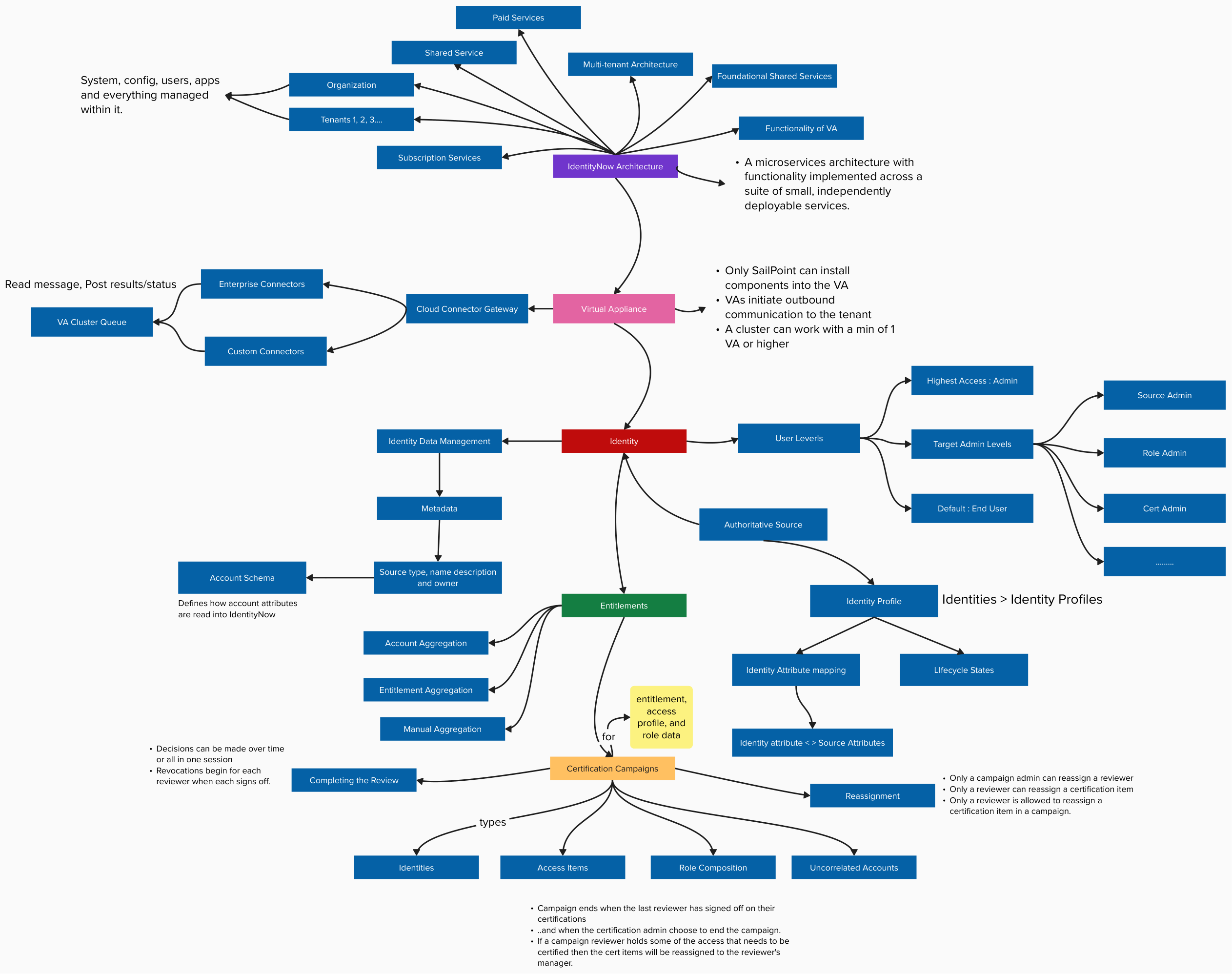
Sayed M

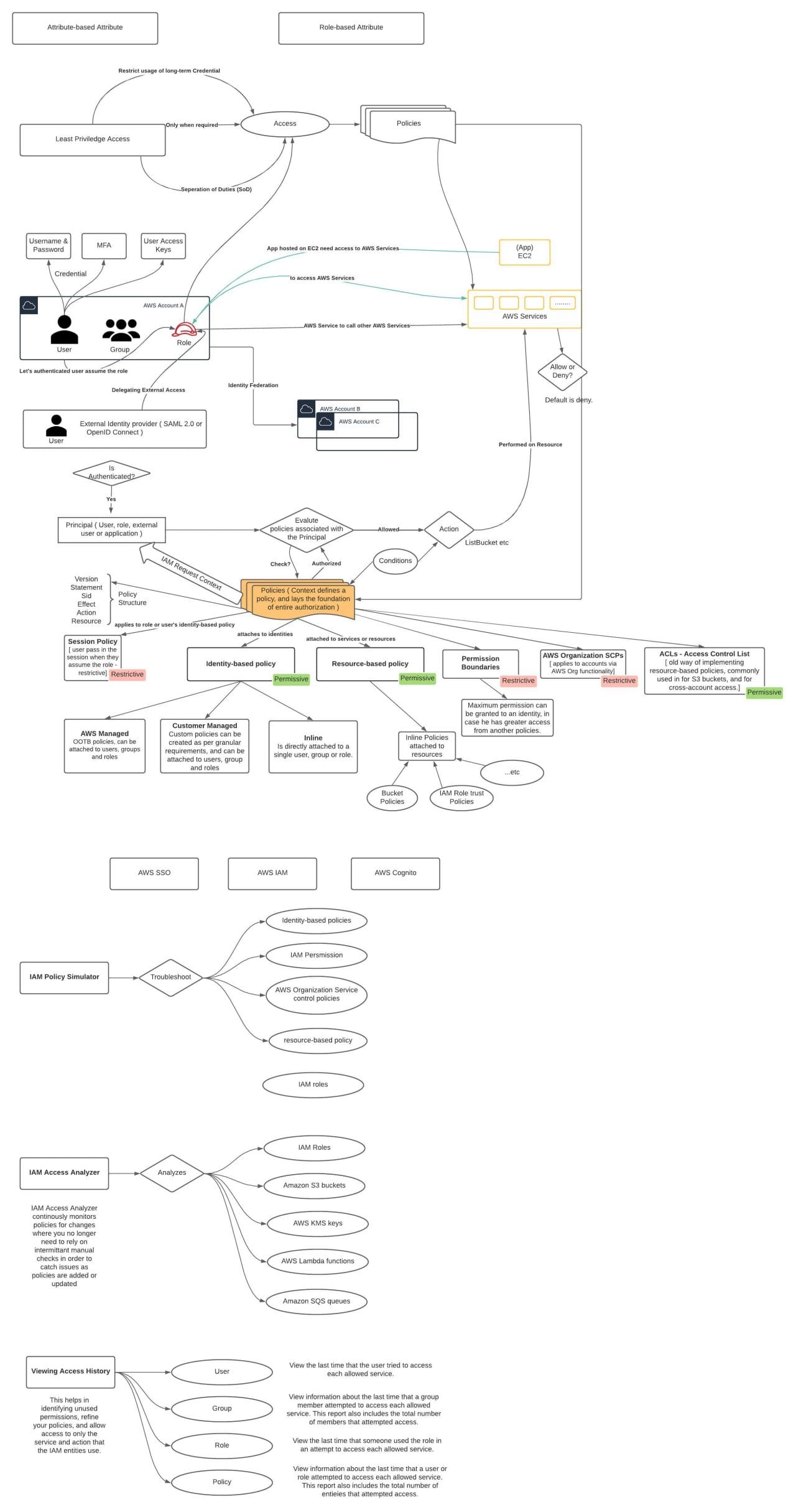
AWS IAM 101

Everything to know about Encryption and Browser Security
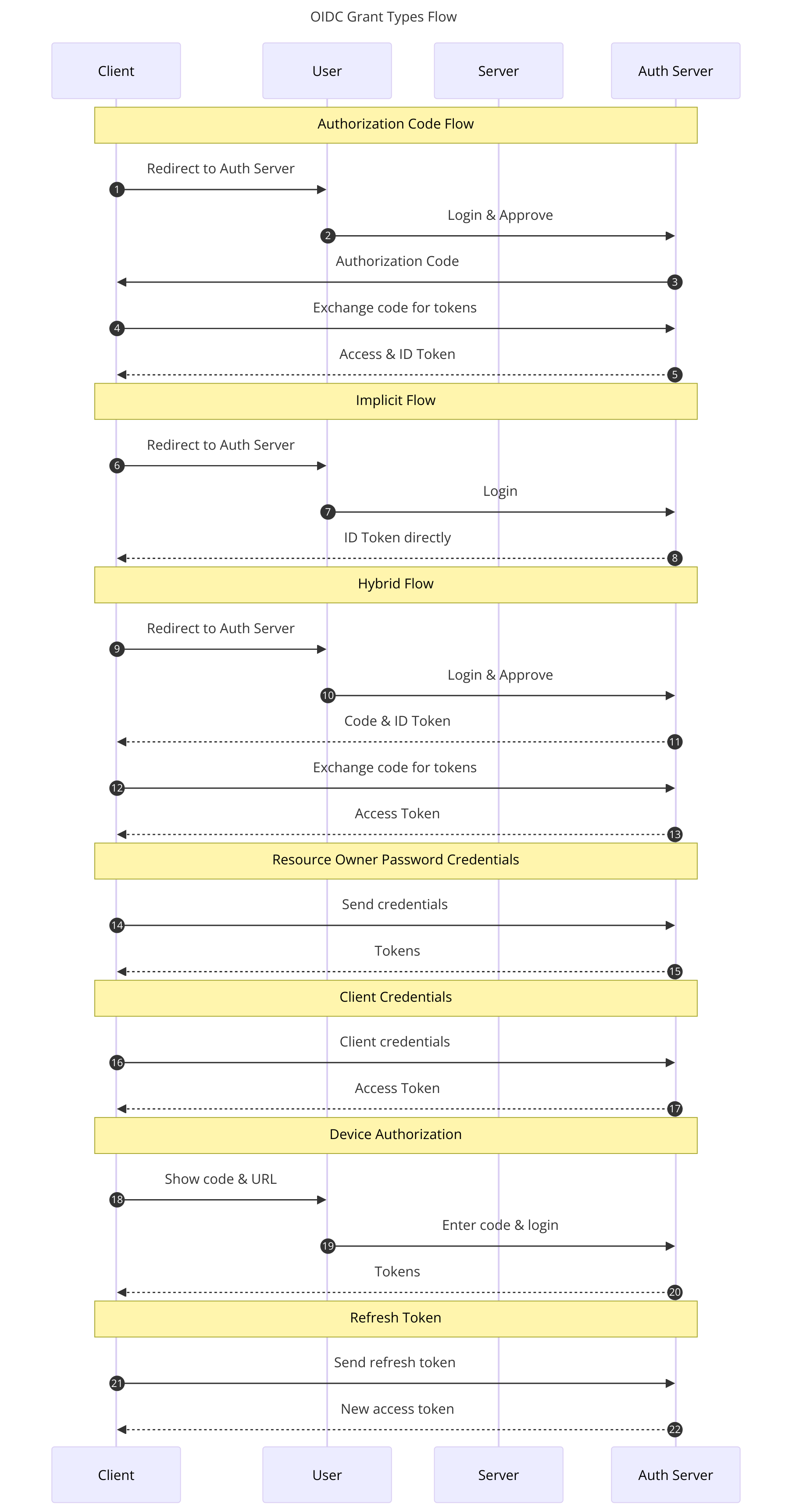
Various OIDC Grants

IAM/Okta Interview Questions
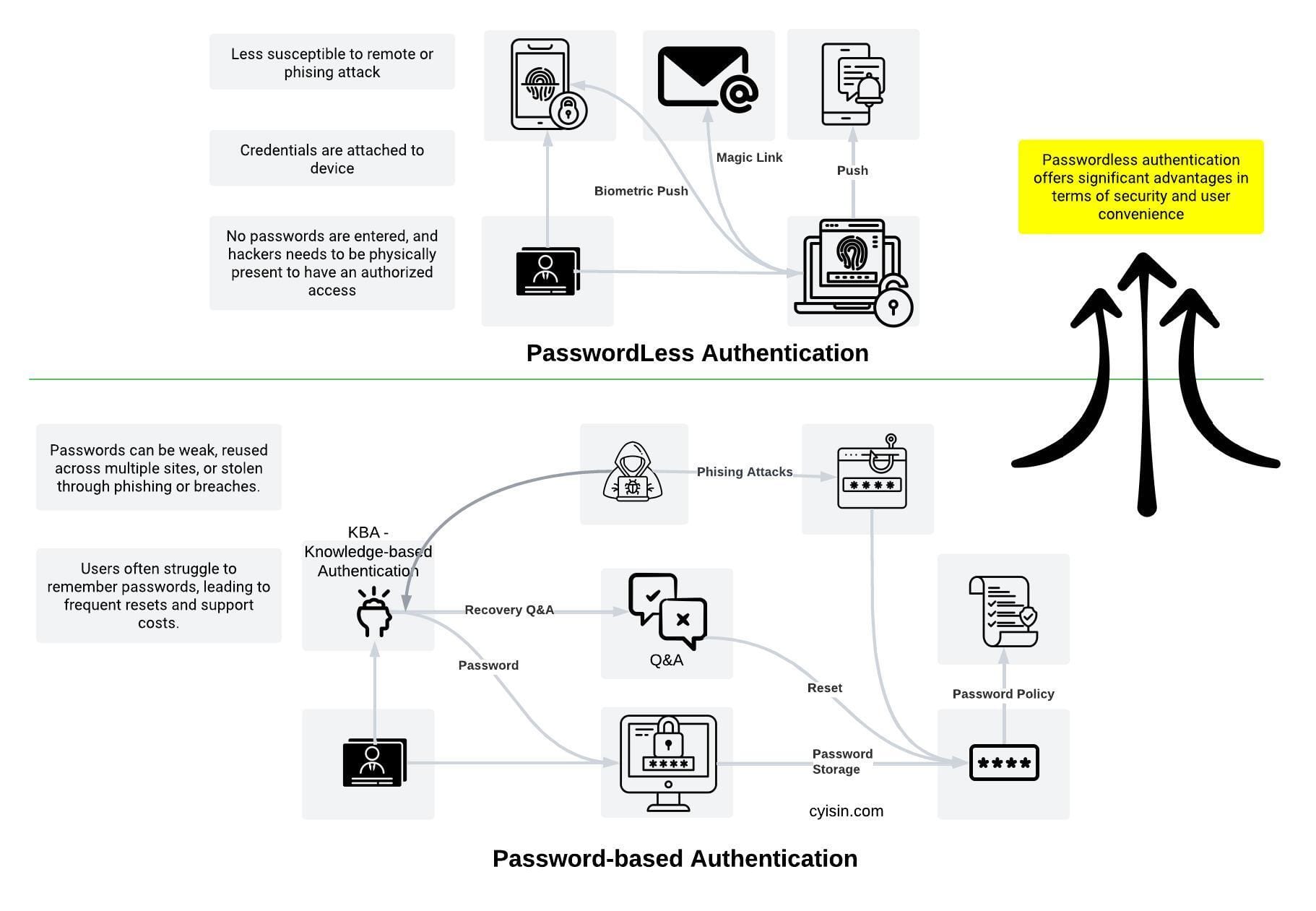
What is PasswordLess Authentication?
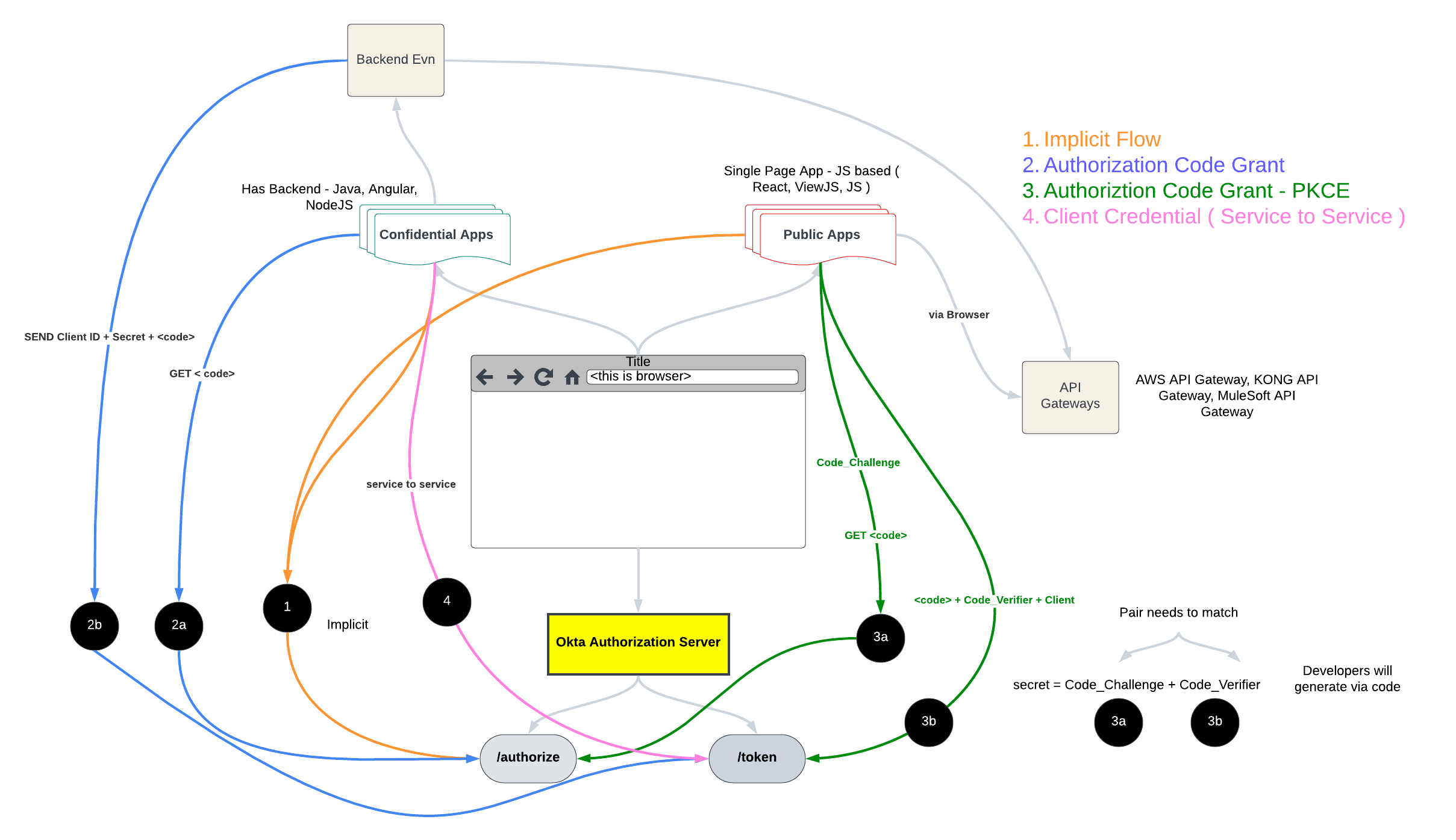
Types of Application - Confidential vs Public Clients
I have asked this question multiple times during Interviews :
What are the
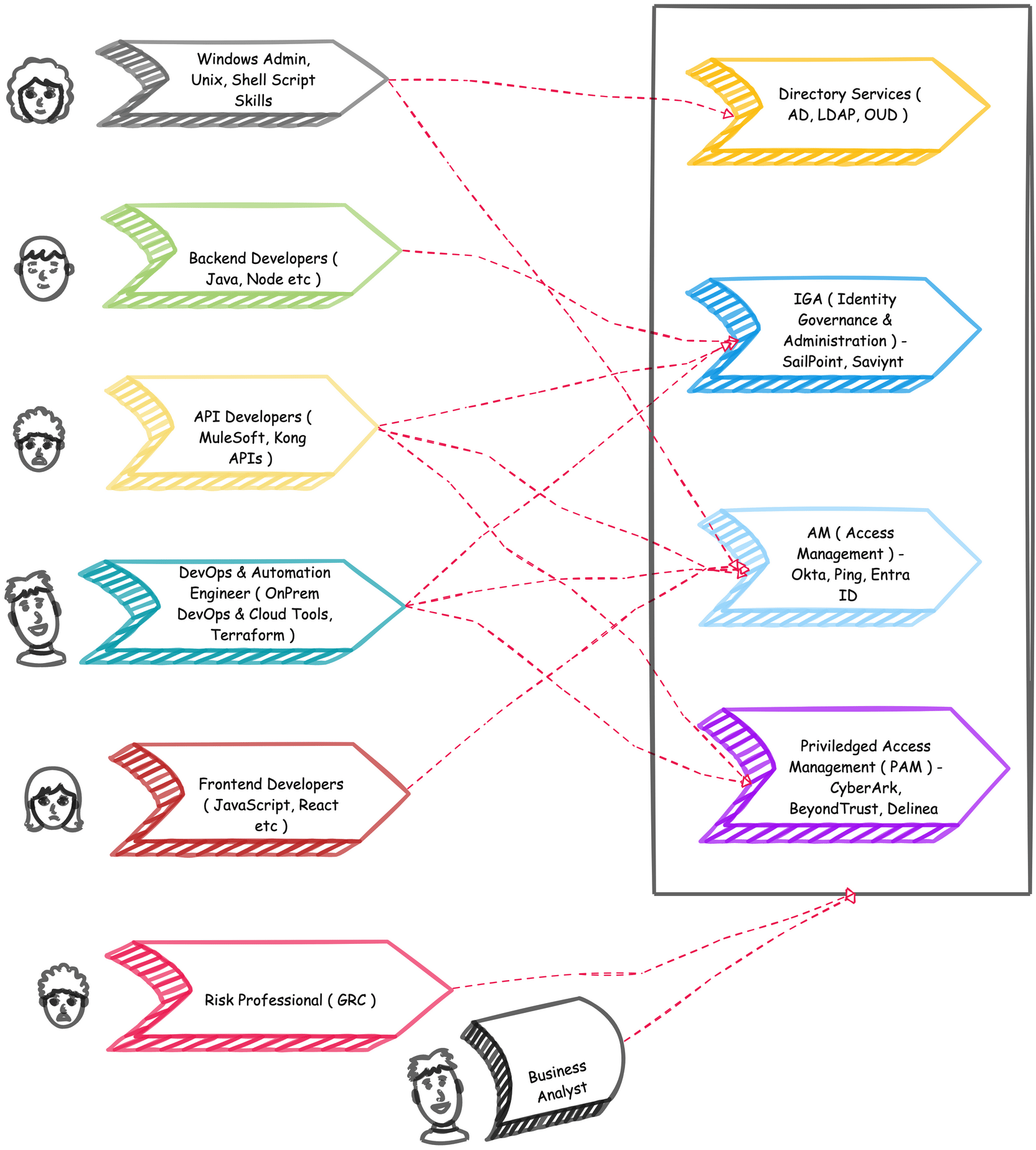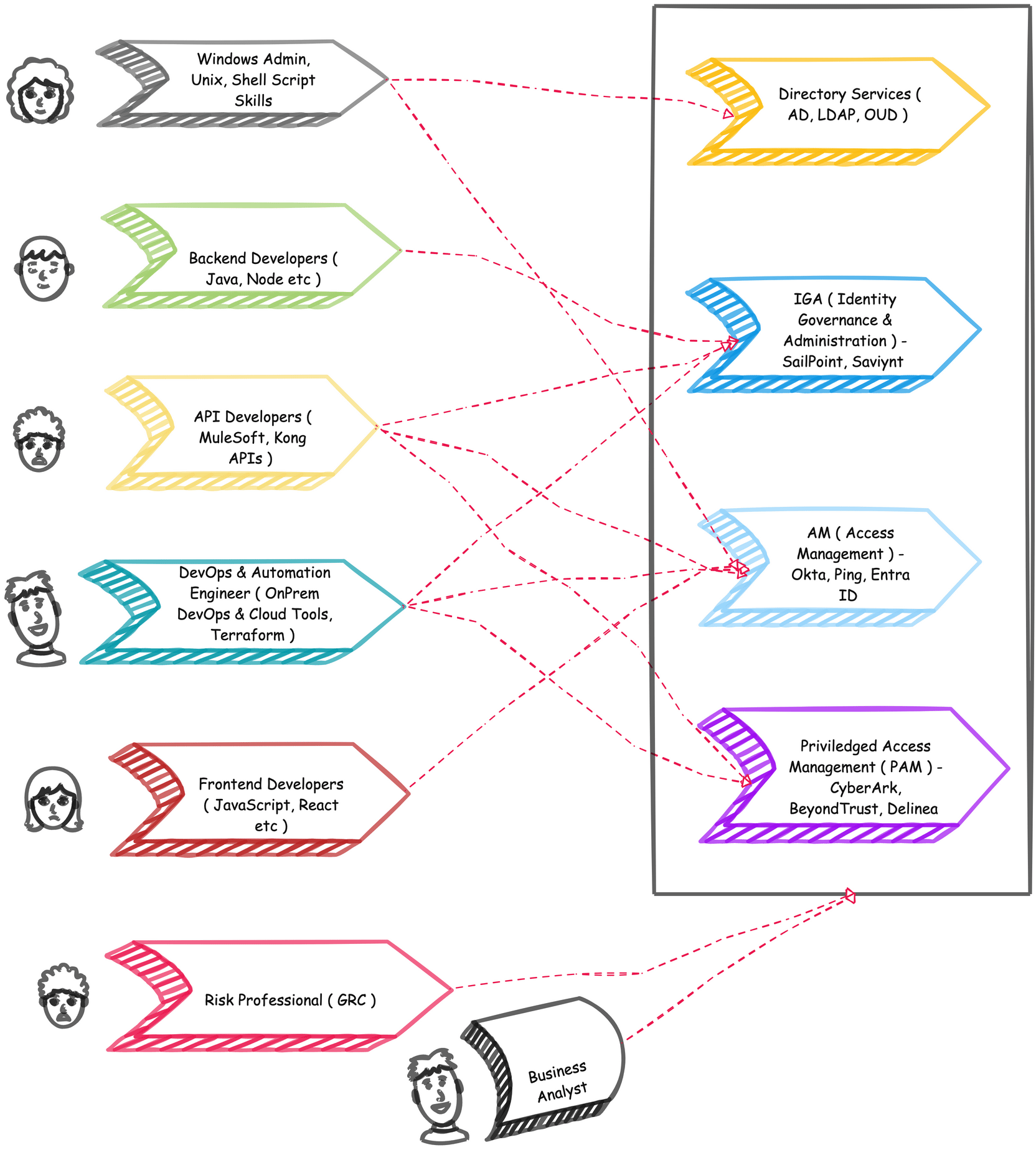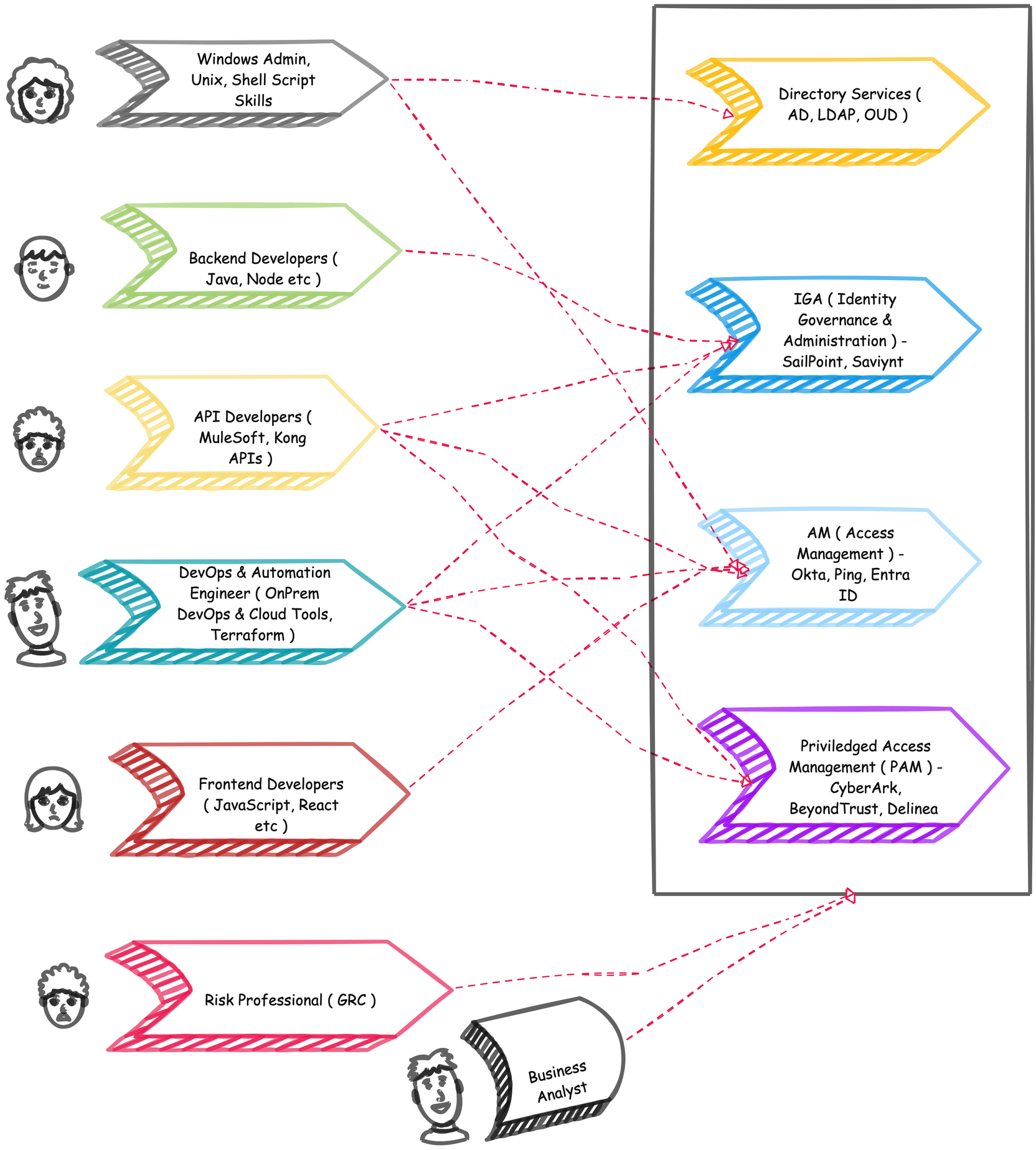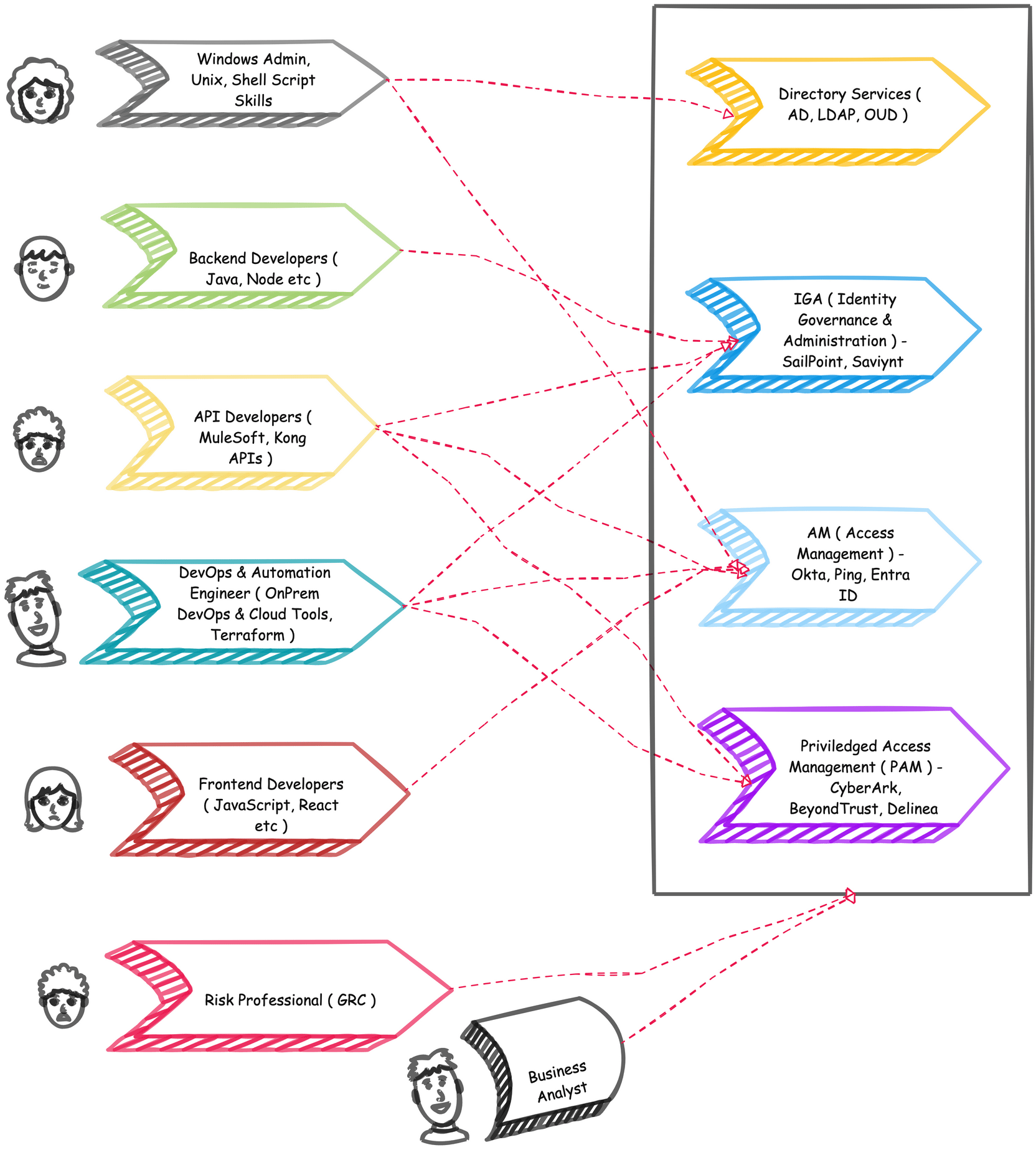
IAM Skill Roadmap
"Everyone is welcome in IAM", don't get overwhelm
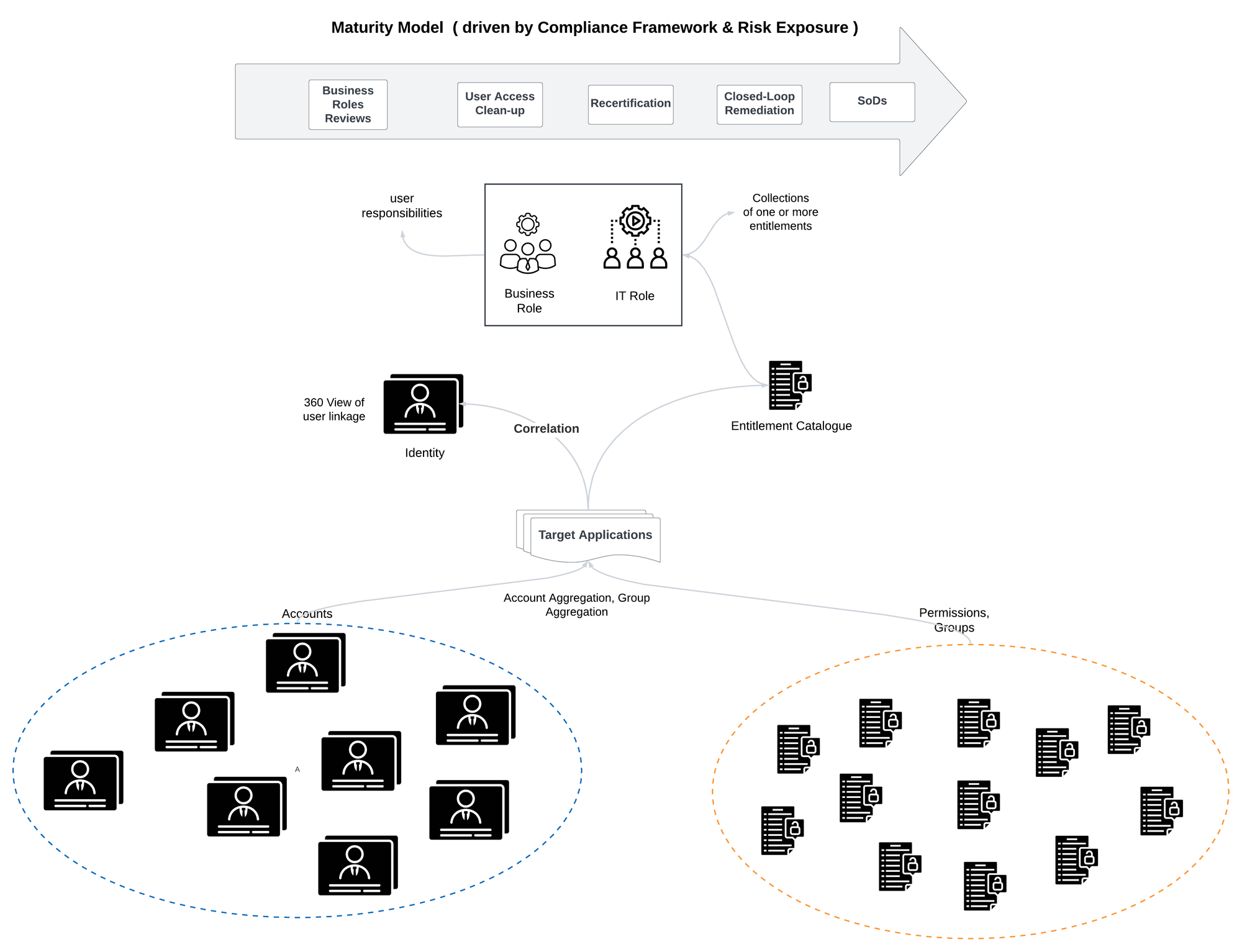
IGA Maturity Model
One of the challenge that we face when implementing IGA tools like
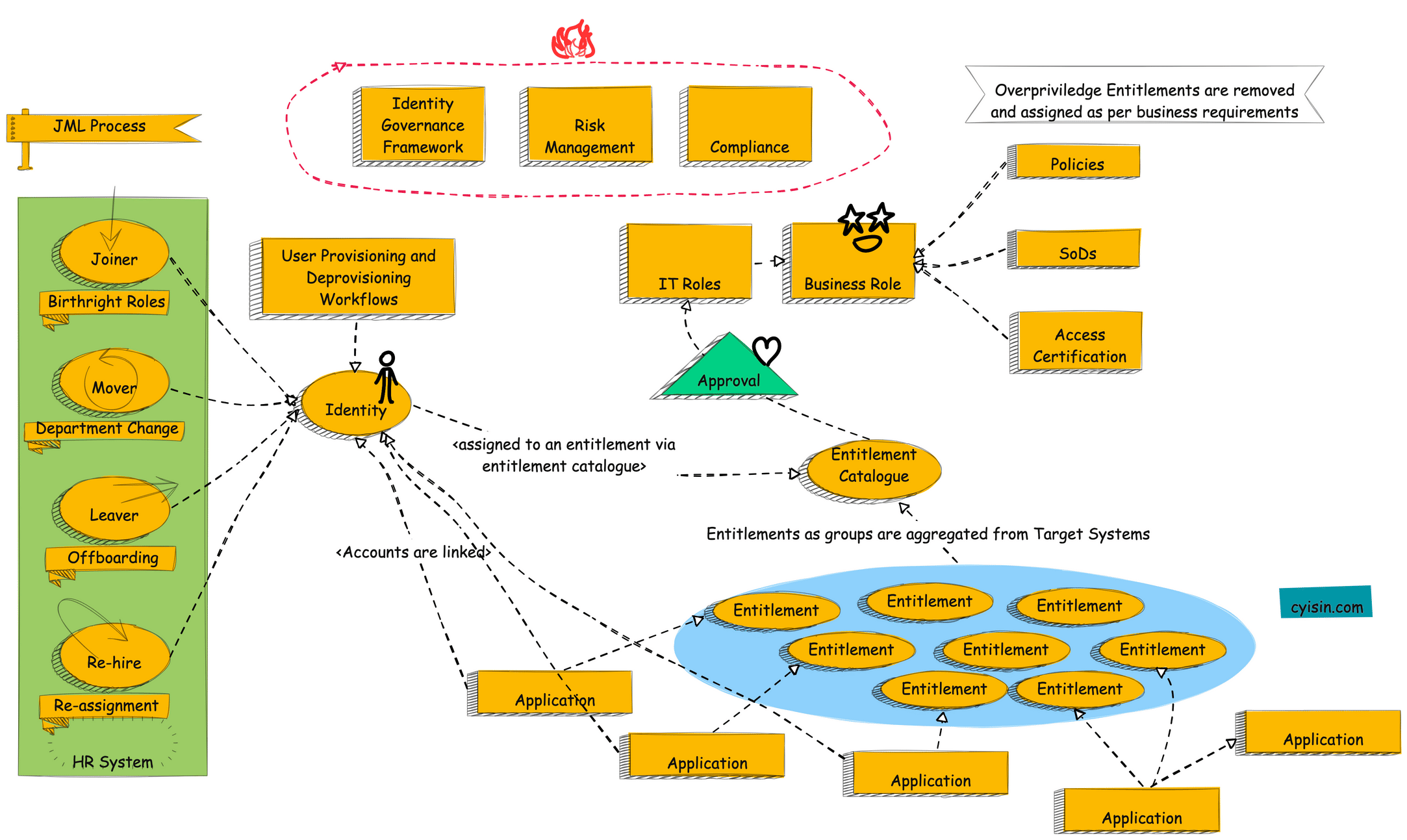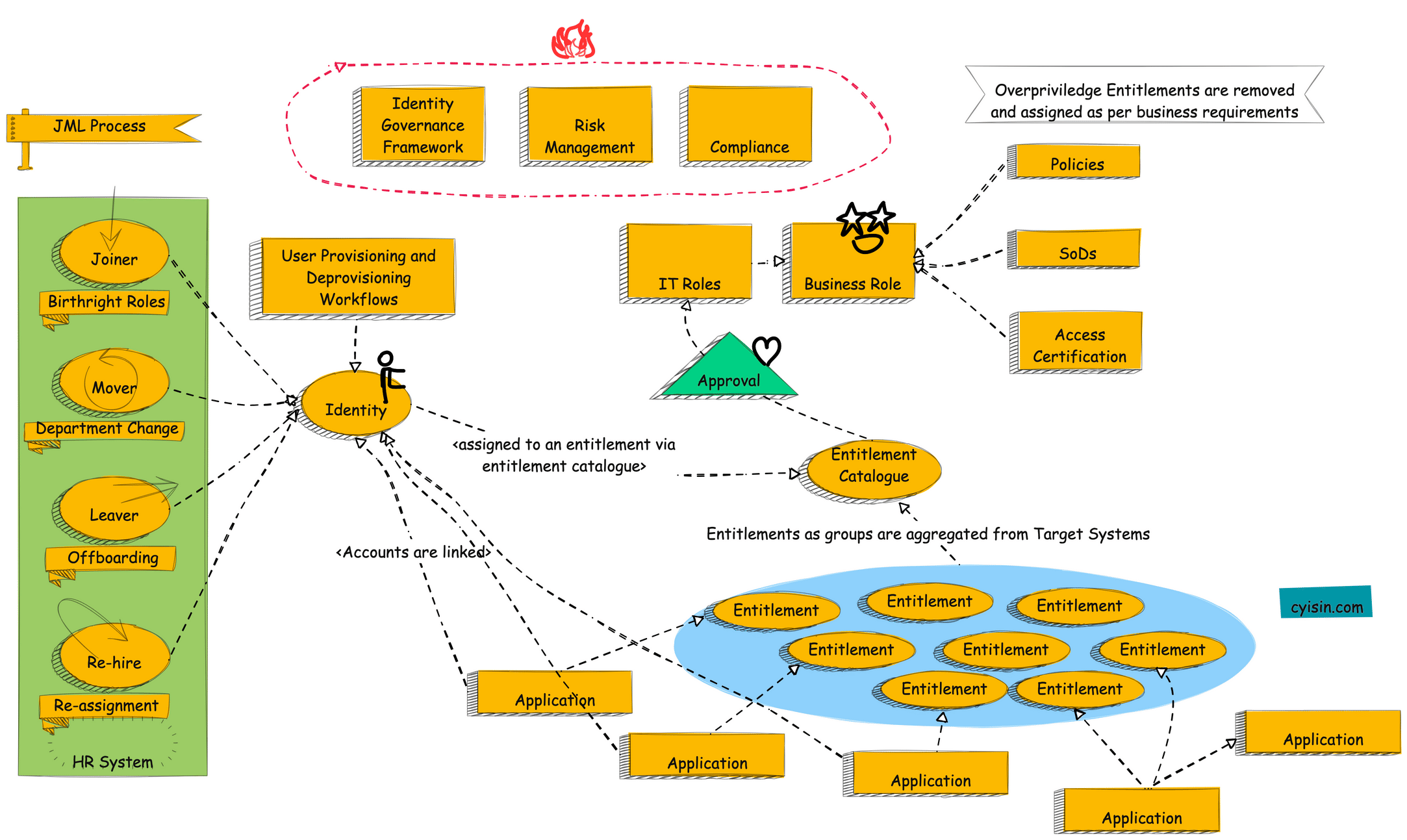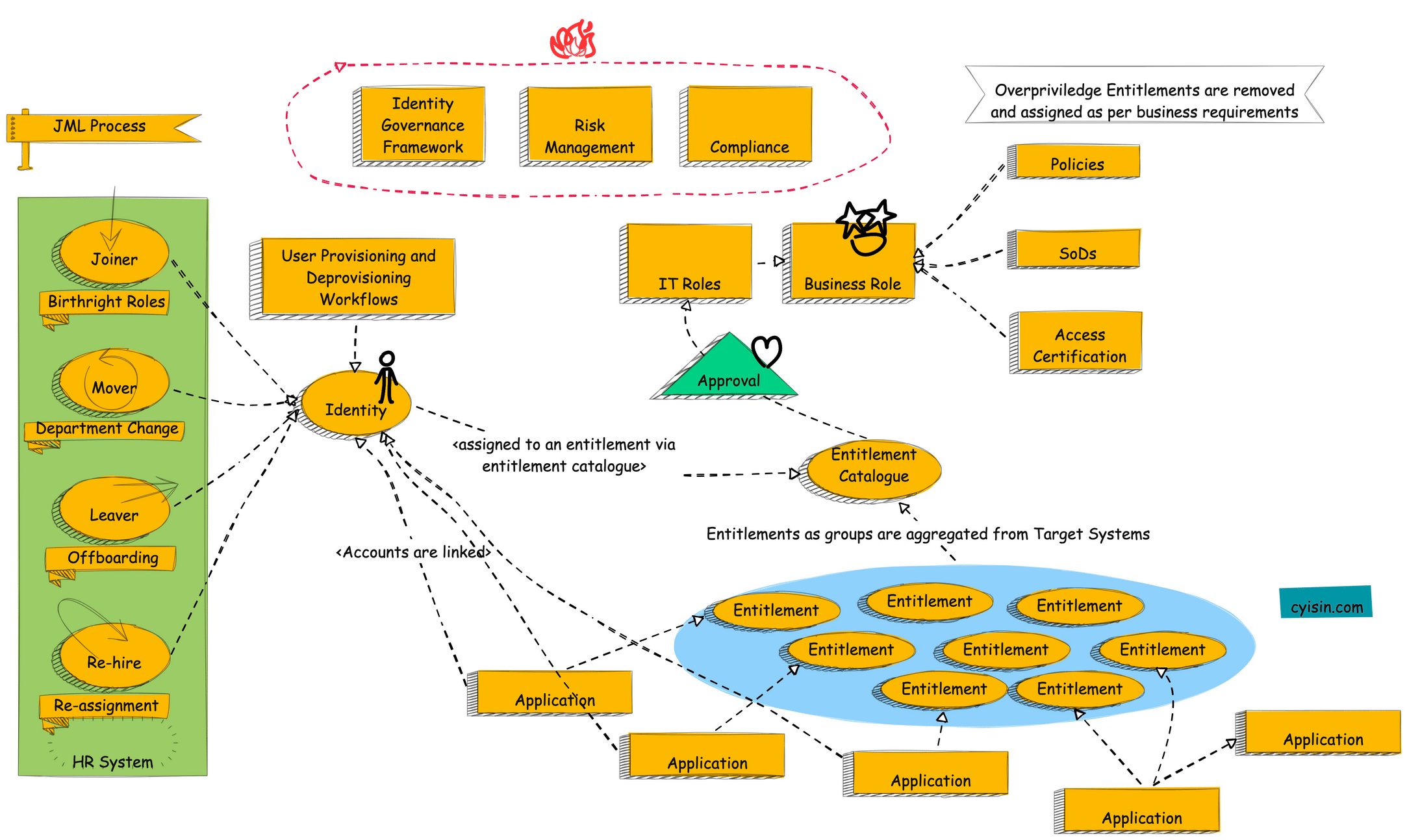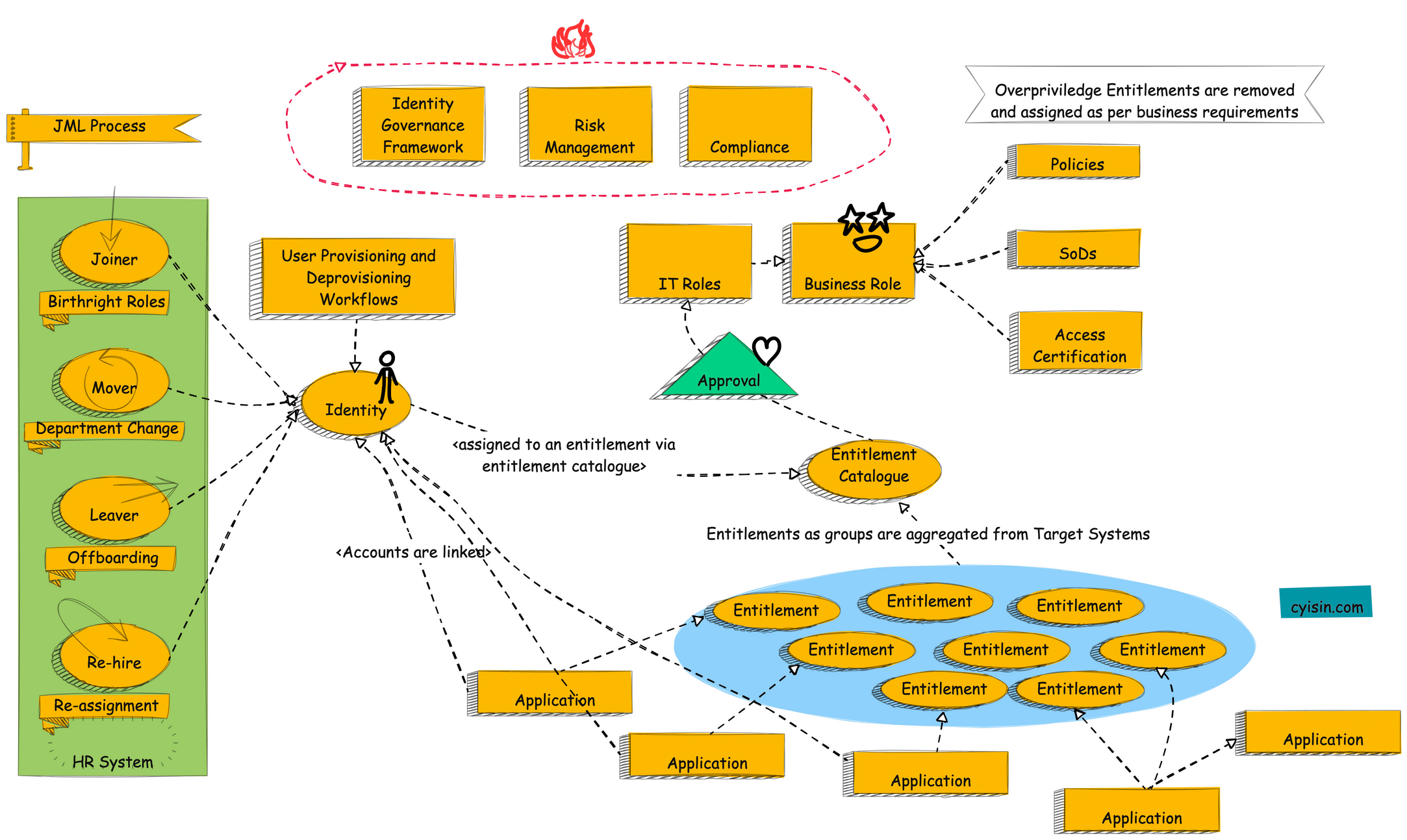
Understanding JML Process in IGA
The attached is a diagram of an Identity Governance Framework (IGF). An
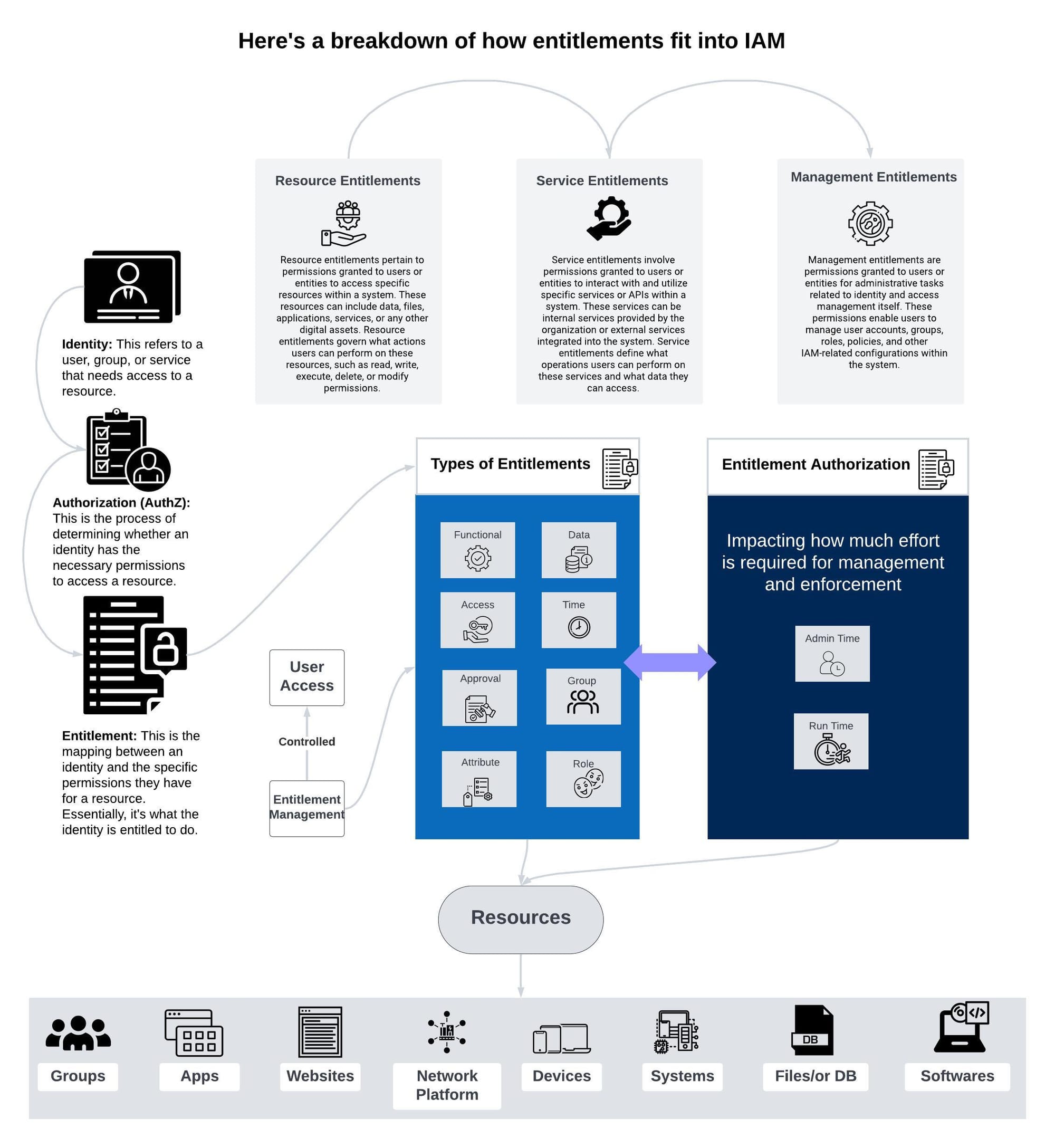
What is Entitlement ?
Entitlements refer to the specific permissions or rights granted to users or
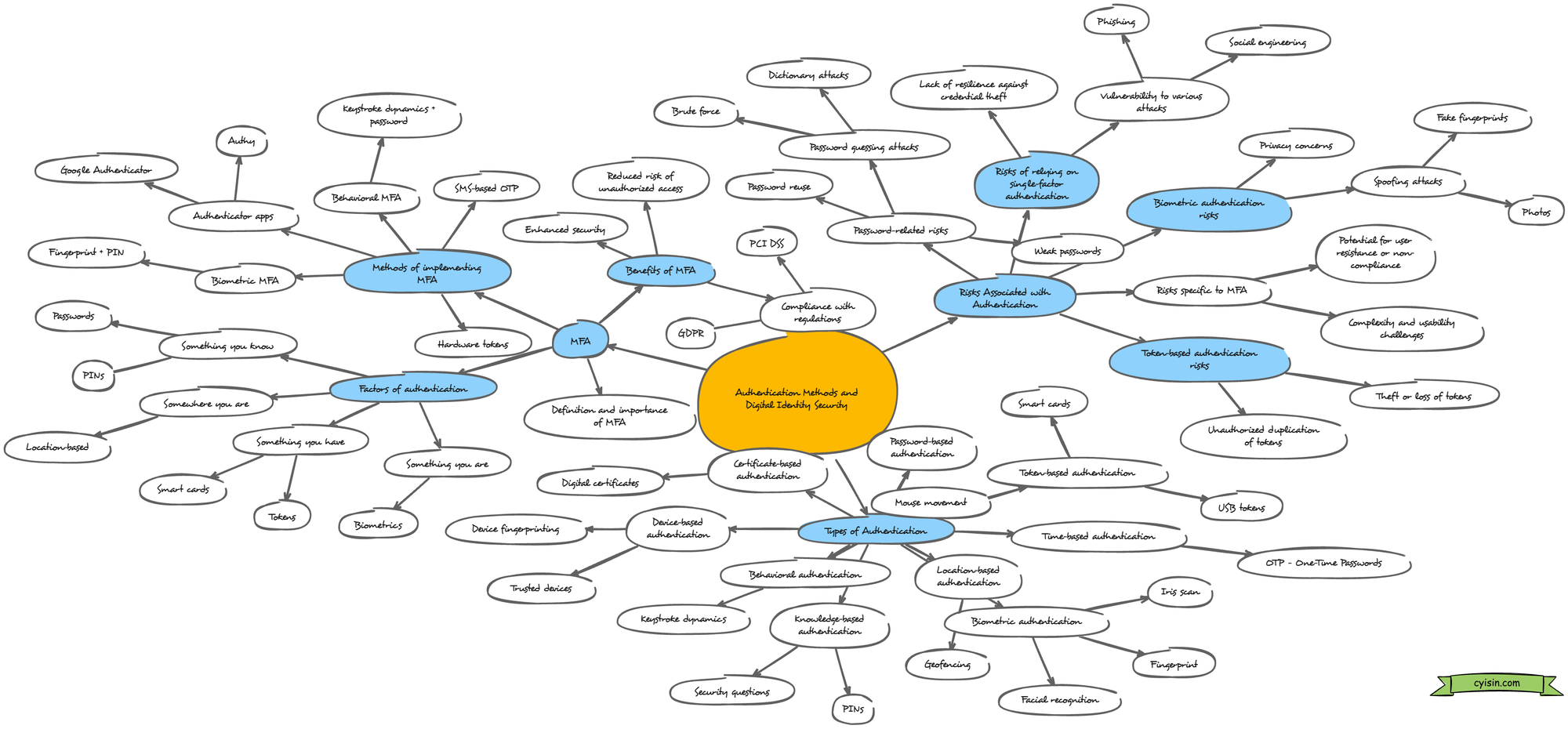
Authentication in the context of Digital Identity
Types of Authentication:
Here's a breakdown of the different authentication
